【wine】【逆向】vb程序自定义窗口最大化崩溃分析EXCEPTION_FLT_INEXACT_RESULT 【2】被加密了
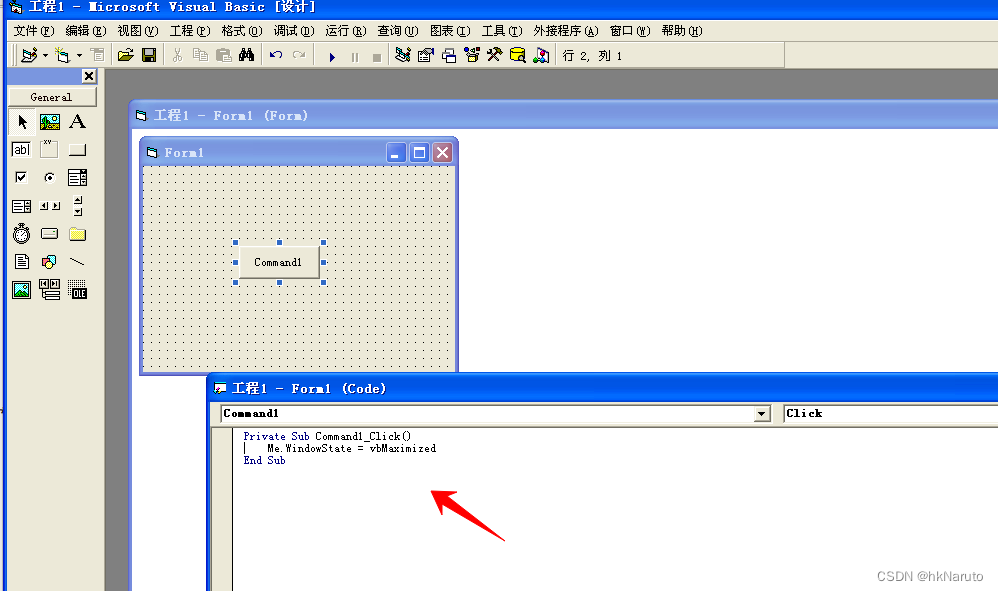
ollydbg在4b6f82下断点,执行。经过vb decompiler, PEID分析,其携带了overlay数据段,应该是被加密了。一段事件的分析后,发现这个程序极大可能被混淆了0x4b6f82处不是一段程序逻辑汇编代码。用windows xp 虚拟机,安装vb6环境,编写一个窗口最大化按钮实现的程序。复制该程序到故障发生的.wine/drive_c/目录下,启动测试。以下是4b6f82在vb
接上篇
【wine】vb程序自定义窗口最大化崩溃分析EXCEPTION_FLT_INEXACT_RESULT 失败-CSDN博客
用windows xp 虚拟机,安装vb6环境,编写一个窗口最大化按钮实现的程序

复制该程序到故障发生的.wine/drive_c/目录下,启动测试
#!/bin/bash
export WINEPREFIX=$(pwd)/.wine
export WINESERVER=$(pwd)/bin/wineserver
export WINELOADER=$(pwd)/bin/wine
export WINEPATH=$(pwd)/bin
export WINEARCH=win32
./bin/wine "c:/vb-maximize.exe"没有崩溃i,功能正常!
再次把问题限制在窗体变动,重新绘图时引发的故障
0024:Call KERNEL32.RaiseException(c000008f,00000001,00000002,0021e3b0) ret=660d0956 ... 0024:warn:seh:dispatch_exception EXCEPTION_FLT_INEXACT_RESULT exception (code=c000008f) raised
往上翻阅日志
0024:trace:heap:RtlAllocateHeap handle 00AC0000, flags 0, size 0x10, return 0371A1D0, status 0.
0024:Ret ntdll.RtlAllocateHeap() retval=0371a1d0 ret=6aaf1b56
0024:Ret ucrtbase._wcsdup() retval=0371a1d0 ret=684d075f
0024:Call ucrtbase.free(00000000) ret=684d07c6
0024:Call KERNEL32.HeapFree(00ac0000,00000000,00000000) ret=6aaf1bc2
0024:Ret KERNEL32.HeapFree() retval=00000001 ret=6aaf1bc2
0024:Ret ucrtbase.free() retval=00000001 ret=684d07c6
0024:Call ucrtbase._wcsdup(0065dbb4 L"\5b9a\4e49\7684\5e94\7528\7a0b\5e8f\6216\5bf9\8c61\9519\8bef") ret=684d07cf
0024:Call ntdll.RtlAllocateHeap(00ac0000,00000000,0000001a) ret=6aaf1b56
这段对应的中文是:"定义的应用程序或对象错误"
过滤出0024,继续往上翻阅日志
0024:Ret KERNEL32.CompareStringA() retval=00000002 ret=6601e62f
0024:Call oleaut32.SysFreeString(0067c9cc L"TypeApp") ret=6600e1a9
0024:Call ntdll.RtlSizeHeap(00340000,00000000,0067c9c8) ret=684d25e1
0024:trace:heap:RtlSizeHeap handle 00340000, flags 0, ptr 0067C9C8, return 0x20, status 0.
0024:Ret ntdll.RtlSizeHeap() retval=00000020 ret=684d25e1
0024:Ret oleaut32.SysFreeString() retval=00000000 ret=6600e1a9
0024:Call oleaut32.SysFreeString(0065dbb4 L"\5b9a\4e49\7684\5e94\7528\7a0b\5e8f\6216\5bf9\8c61\9519\8bef") ret=6600e1ae
0024:Call ntdll.RtlSizeHeap(00340000,00000000,0065dbb0) ret=684d25e1
0024:trace:heap:RtlSizeHeap handle 00340000, flags 0, ptr 0065DBB0, return 0x20, status 0.
0024:Ret ntdll.RtlSizeHeap() retval=00000020 ret=684d25e1
0024:Ret oleaut32.SysFreeString() retval=00000000 ret=6600e1ae
0024:Call oleaut32.SysFreeString(00000000) ret=6600e1b3
0024:Ret oleaut32.SysFreeString() retval=684ea1d8 ret=6600e1b3
0024:Call KERNEL32.MultiByteToWideChar(00000000,00000000,11007ce0 "ImageX",ffffffff,00000000,00000000) ret=660da0b1
0024:Call ntdll.strlen(11007ce0 "ImageX") ret=7b031dda
0024:Ret ntdll.strlen() retval=00000006 ret=7b031dda
0024:Ret KERNEL32.MultiByteToWideChar() retval=00000007 ret=660da0b1
0024:Call oleaut32.SysAllocStringLen(00000000,00000006) ret=660da0bc
0024:Call ucrtbase.memset(0065c5c8,00000055,00000012) ret=62506bf6
0024:Ret ucrtbase.memset() retval=0065c5c8 ret=62506bf6
0024:Call ucrtbase.memset(0065c5da,000000ab,0000000e) ret=62506c14
0024:Ret ucrtbase.memset() retval=0065c5da ret=62506c14
0024:Call ucrtbase.memset(0065c5cc,00000000,0000000e) ret=62507b67
0024:Ret ucrtbase.memset() retval=0065c5cc ret=62507b67
0024:Ret oleaut32.SysAllocStringLen() retval=0065c5cc ret=660da0bc
0024:Call KERNEL32.MultiByteToWideChar(00000000,00000000,11007ce0 "ImageX",ffffffff,0065c5cc,00000007) ret=660da0db
0024:Call ntdll.strlen(11007ce0 "ImageX") ret=7b031dda
0024:Ret ntdll.strlen() retval=00000006 ret=7b031dda
0024:Ret KERNEL32.MultiByteToWideChar() retval=00000007 ret=660da0db
0024:Call KERNEL32.RaiseException(c000008f,00000001,00000002,0021f110) ret=660d0956
0024:trace:seh:dispatch_exception code=c000008f flags=1 addr=7B011DC4 ip=7b011dc4
0024:trace:seh:dispatch_exception info[0]=deadcafe
0024:trace:seh:dispatch_exception info[1]=deadcafe
0024:warn:seh:dispatch_exception EXCEPTION_FLT_INEXACT_RESULT exception (code=c000008f) raised
0024:trace:seh:dispatch_exception eax=0021f060 ebx=deadcafe ecx=00000004 edx=0021f110 esi=0021f110 edi=0021f0d0
0024:trace:seh:dispatch_exception ebp=0021f0b8 esp=0021f054 cs=1fc0023 ss=21002b ds=21002b es=002b fs=210063 gs=7bc4006b flags=00000246
0024:trace:seh:call_stack_handlers calling handler at 11003D56 code=c000008f flags=1
0024:Call KERNEL32.IsBadReadPtr(110016a8,00000004) ret=660e3cfd
0024:Ret KERNEL32.IsBadReadPtr() retval=00000000 ret=660e3cfd
0024:trace:seh:__regs_RtlUnwind code=c0000027 flags=2
0024:trace:seh:__regs_RtlUnwind eax=00000000 ebx=7b60e340 ecx=0021f22c edx=7ffc2000 esi=110016a8 edi=0021f22c
0024:trace:seh:__regs_RtlUnwind ebp=0021eafc esp=0021eaf0 eip=66103de0 cs=0023 ds=002b fs=0063 gs=006b flags=00000206
0024:trace:seh:__regs_RtlUnwind calling handler at 7BC5AAC0 code=c0000027 flags=2
0024:trace:seh:__regs_RtlUnwind handler at 7BC5AAC0 returned 1
0024:Call oleaut32.CreateErrorInfo(0021eae0) ret=660d8360
0024:Call combase.CreateErrorInfo(0021eae0) ret=7bc4b9f4
0024:Call ucrtbase.malloc(00000030) ret=684d0e08
0024:Call ntdll.RtlAllocateHeap(00ac0000,00000000,00000030) ret=6aaf1b56
0024:trace:heap:RtlAllocateHeap handle 00AC0000, flags 0, size 0x30, return 00AC4FA0, status 0.
直接逆向,禁用调这个按钮
下载 VB Decompiler
vb decompiler pro 注册码|vb decompiler pro (VB反编译工具) 10.1 汉化破解版-闪电软件园

试试直接删除调所有BtnMax按钮时间处理代码
vb decompiler 不能修改代码?
ollydbg在4b6f82下断点,执行。似乎断点位置不对。不过也发现这个程序在windows平台下也会有异常触发

一段事件的分析后,发现这个程序极大可能被混淆了0x4b6f82处不是一段程序逻辑汇编代码。
以下是4b6f82在vb decompiler里面的反汇编

ollydbg返回编不一致

这又触及到知识盲区了。。。
尝试通过Maximize找


自己编写一个简单的vb6程序,对比

自己编写的程序未被混淆,代码位置正确,目标程序位置对应不上
可以看到401290位置极为可疑,应该是加密数据的开头。
pe explorer查看入口地址

CALL MSVBVM60.7339365C后,窗体弹出


进入了这个循环

经过vb decompiler, PEID分析,其携带了overlay数据段,应该是被加密了。
实力不足,放弃
更多推荐
 已为社区贡献46条内容
已为社区贡献46条内容









所有评论(0)