OSCP靶机练习--CuteNews01
靶机地址:BBS (cute): 1.0.2 ~ VulnHub靶机环境搭建:个人本地环境:VMWare已经安装好了,因为虚拟机镜像是virtualBox的.vbox结尾,所以在本地又安装了VitualBoxVMWare和VitualBox的NAT网络不能同时使用, 整了半天也没搞起来,后来才知道这两种虚拟程序不能同时使用NAT。所以使用了另外一台Kali的机器,直接用主机来测了。靶机本地用Vir
目录
靶机地址:BBS (cute): 1.0.2 ~ VulnHub
靶机地址:BBS (cute): 1.0.2 ~ VulnHub
靶机环境搭建:
个人本地环境:VMWare已经安装好了,因为虚拟机镜像是virtualBox的.vbox结尾,所以在本地又安装了VitualBox
VMWare和VitualBox的NAT网络不能同时使用, 整了半天也没搞起来,后来才知道这两种虚拟程序不能同时使用NAT。
所以使用了另外一台Kali的机器,直接用主机来测了。靶机本地用VirtualBox安装靶机。
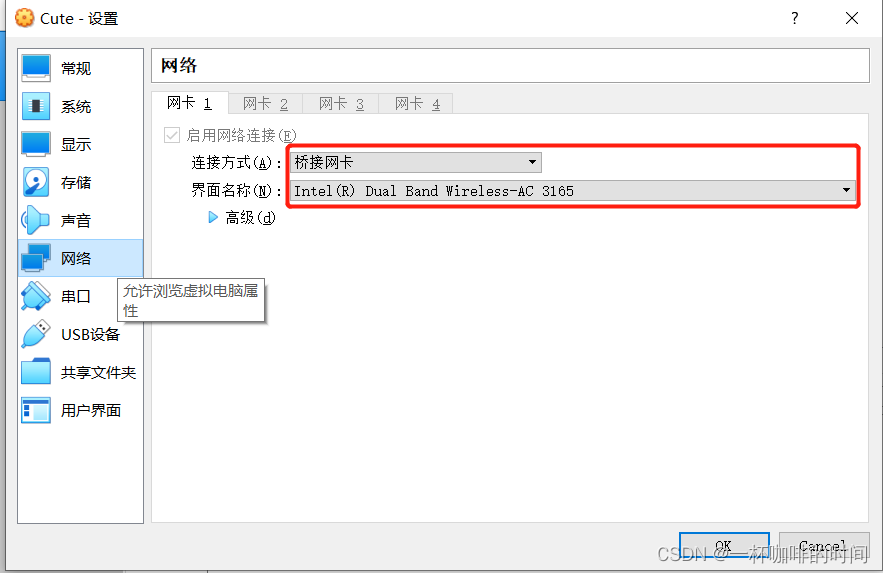
但因为不在同一台机器上面,所以才用的是桥接的方式链接,如下:
信息收集:
1. IP地址确认:
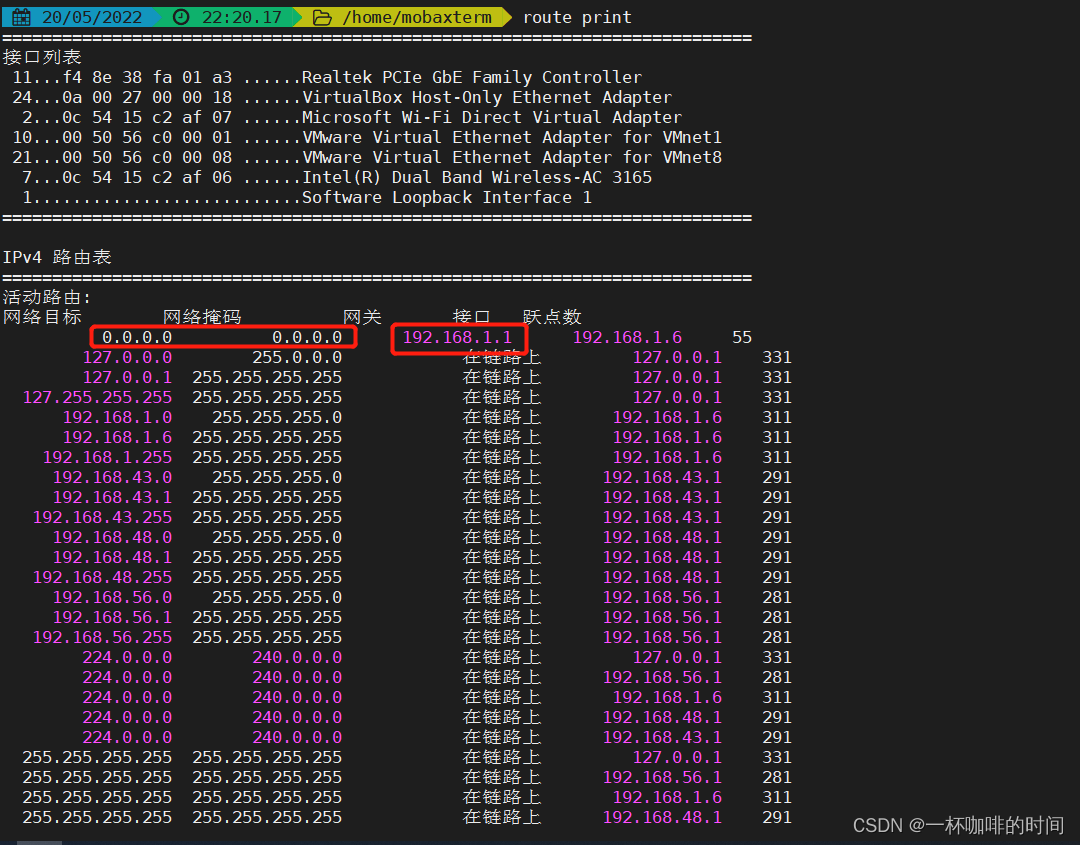
本地路由信息如下:
2. 确认virtualBox上面的靶机地址:
nmap -p- -top 10 192.168.1.1/24
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-20 22:22 CST
Nmap scan report for 192.168.1.1
Host is up (0.0042s latency).
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp closed ssh
23/tcp open telnet
25/tcp closed smtp
80/tcp open http
110/tcp closed pop3
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp open microsoft-ds
3389/tcp closed ms-wbt-server
MAC Address: 1C:FF:59:0D:DB:44 (Sichuan Tianyi Comheart Telecom)
Nmap scan report for chuangmi.camera.ipc019 (192.168.1.3)
Host is up (0.0076s latency).
PORT STATE SERVICE
21/tcp closed ftp
22/tcp closed ssh
23/tcp closed telnet
25/tcp closed smtp
80/tcp closed http
110/tcp closed pop3
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
3389/tcp closed ms-wbt-server
MAC Address: 5C:E5:0C:75:A8:F1 (Beijing Xiaomi Mobile Software)
Nmap scan report for B365 (192.168.1.5)
Host is up (0.0047s latency).
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp filtered ssh
23/tcp open telnet
25/tcp filtered smtp
80/tcp open http
110/tcp filtered pop3
139/tcp filtered netbios-ssn
443/tcp open https
445/tcp filtered microsoft-ds
3389/tcp filtered ms-wbt-server
MAC Address: F0:10:90:1E:05:A5 (New H3C Technologies)
Nmap scan report for Fiona-PC (192.168.1.6)
Host is up (0.0083s latency).
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp filtered ssh
23/tcp filtered telnet
25/tcp filtered smtp
80/tcp filtered http
110/tcp filtered pop3
139/tcp open netbios-ssn
443/tcp filtered https
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
MAC Address: 0C:54:15:C2:AF:06 (Intel Corporate)
Nmap scan report for 192.168.1.16
Host is up (0.0095s latency).
PORT STATE SERVICE
21/tcp closed ftp
22/tcp open ssh
23/tcp closed telnet
25/tcp closed smtp
80/tcp open http
110/tcp open pop3
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
3389/tcp closed ms-wbt-server
MAC Address: 0C:54:15:C2:AF:06 (Intel Corporate)
Nmap scan report for F-kali (192.168.1.18)
Host is up (0.000033s latency).
PORT STATE SERVICE
21/tcp closed ftp
22/tcp open ssh
23/tcp closed telnet
25/tcp closed smtp
80/tcp closed http
110/tcp closed pop3
139/tcp closed netbios-ssn
443/tcp closed https
445/tcp closed microsoft-ds
3389/tcp closed ms-wbt-server
Nmap done: 256 IP addresses (6 hosts up) scanned in 8.00 seconds
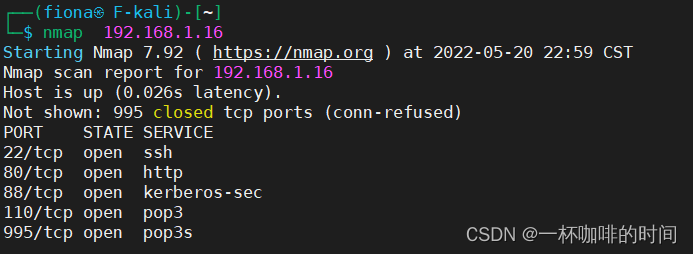
排除家里已知的IP地址,确定靶机ip地址:192.168.1.16.
注意:OSCP考试的时候,IP地址是已经确定好的,不需要上面的这一步。直接从下一步开始。
3. 端口信息收集:
获得端口:nmap 192.168.1.16
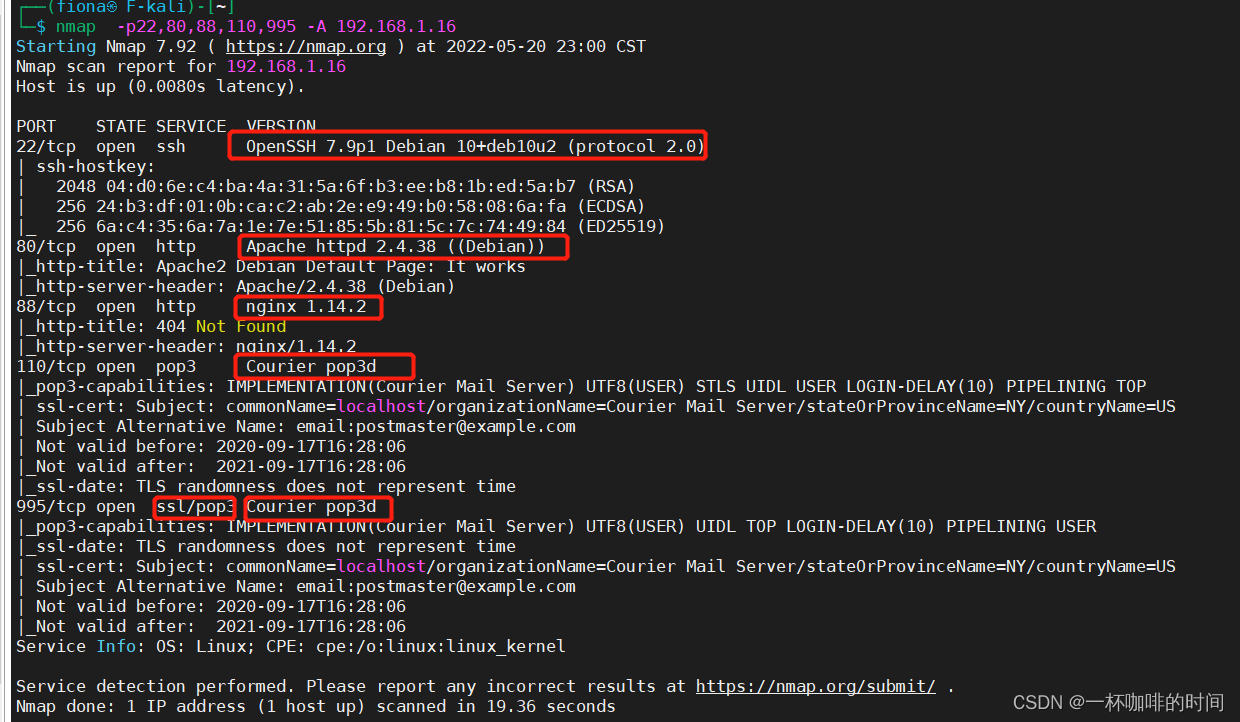
端口信息进一步收集: nmap -p22,80,88,110,995 -A 192.168.1.16
4. 根据上面端口信息内容搜索已有POC
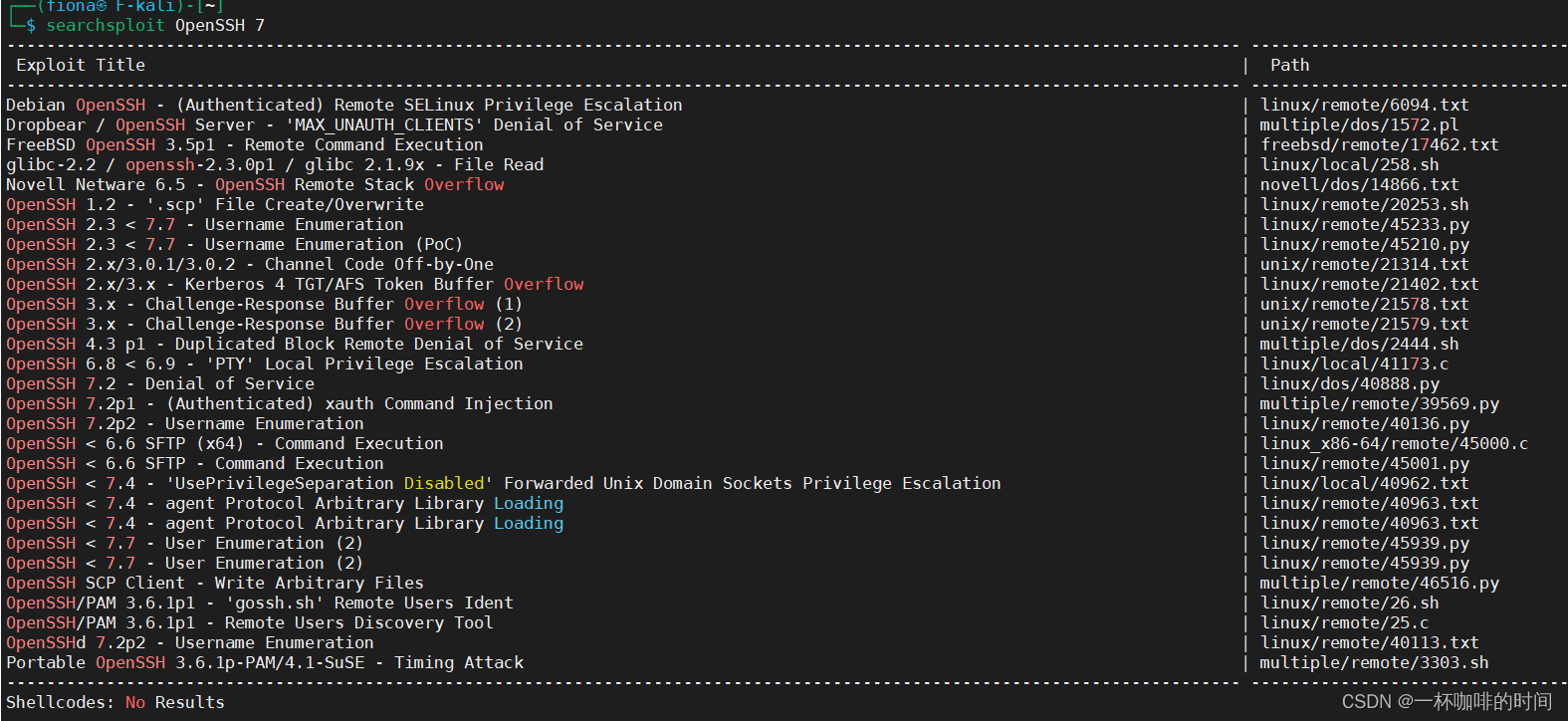
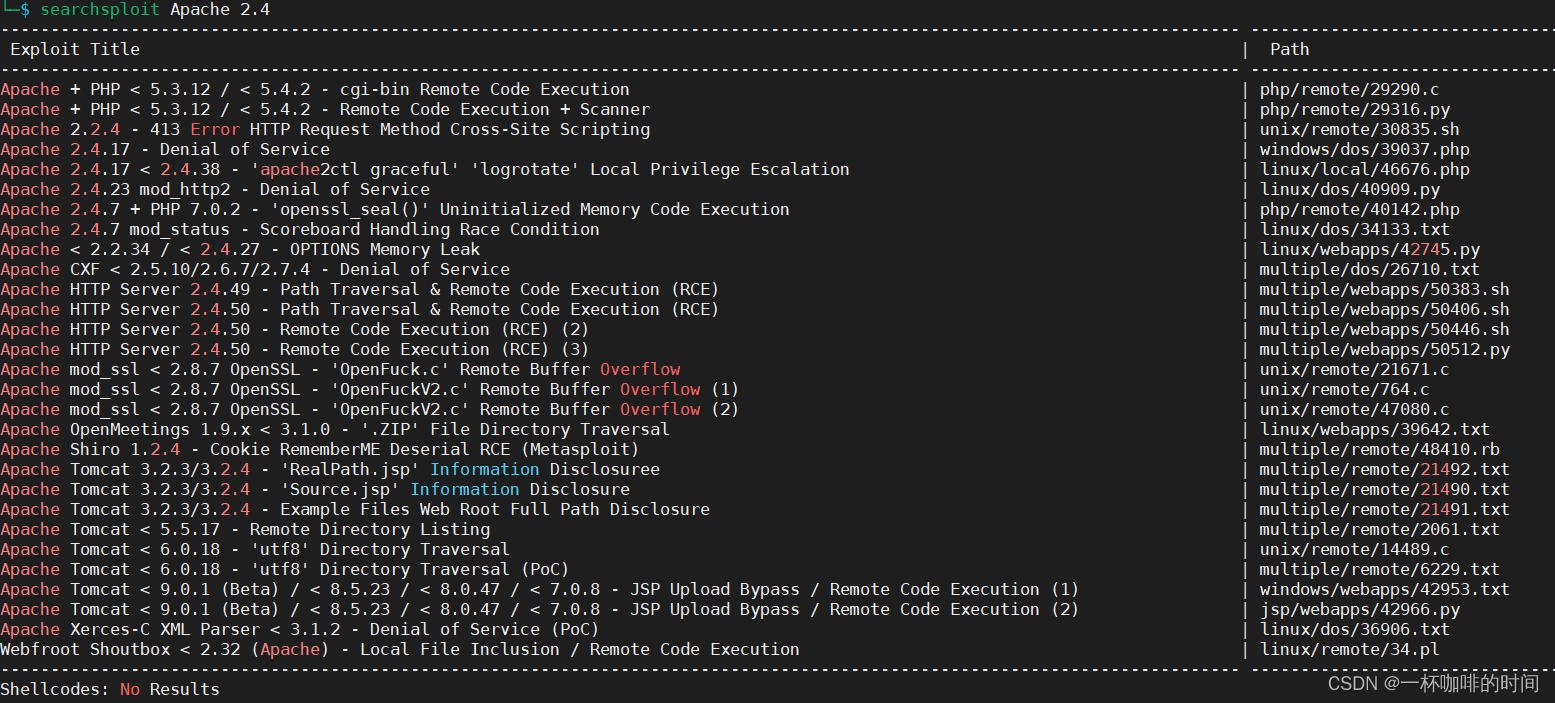
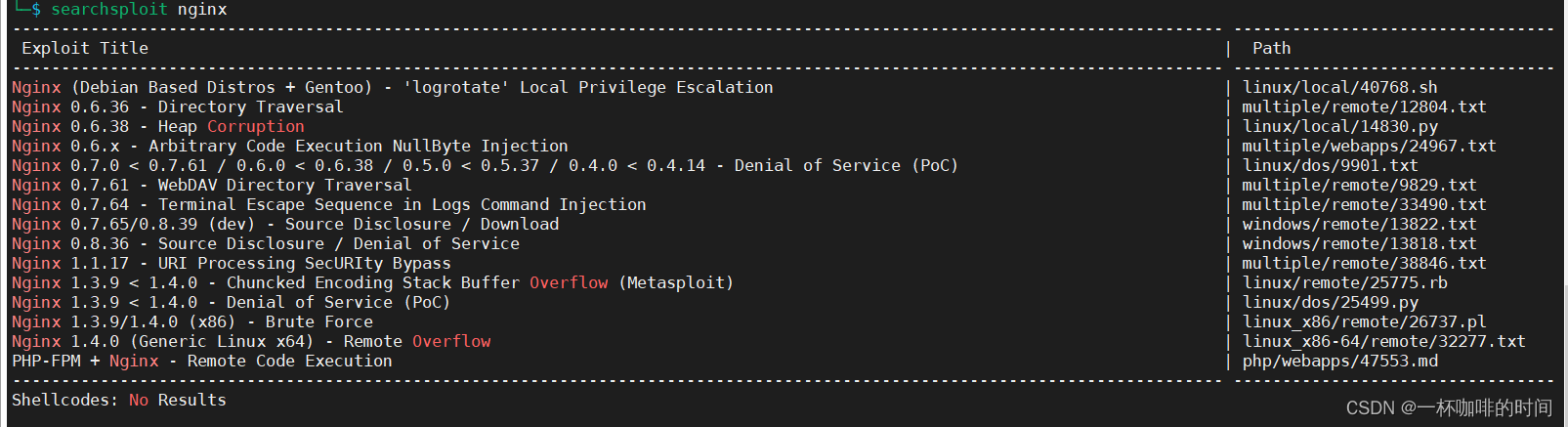
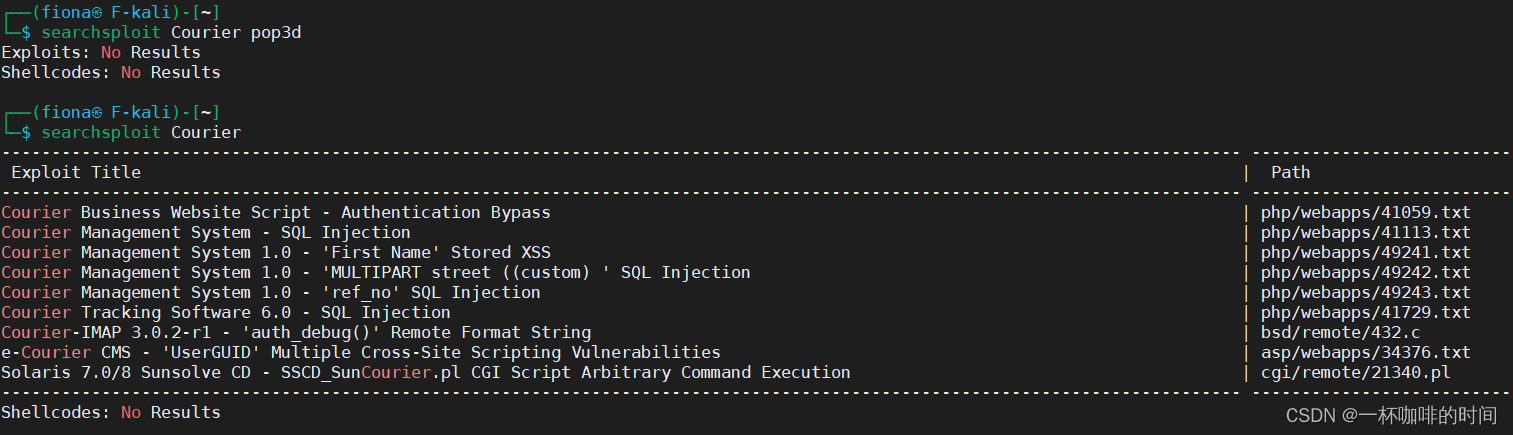
直接根据端口扫描出来的信息提示,没有找到 对应的POC。
5. 根据Web端的信息收集信息:
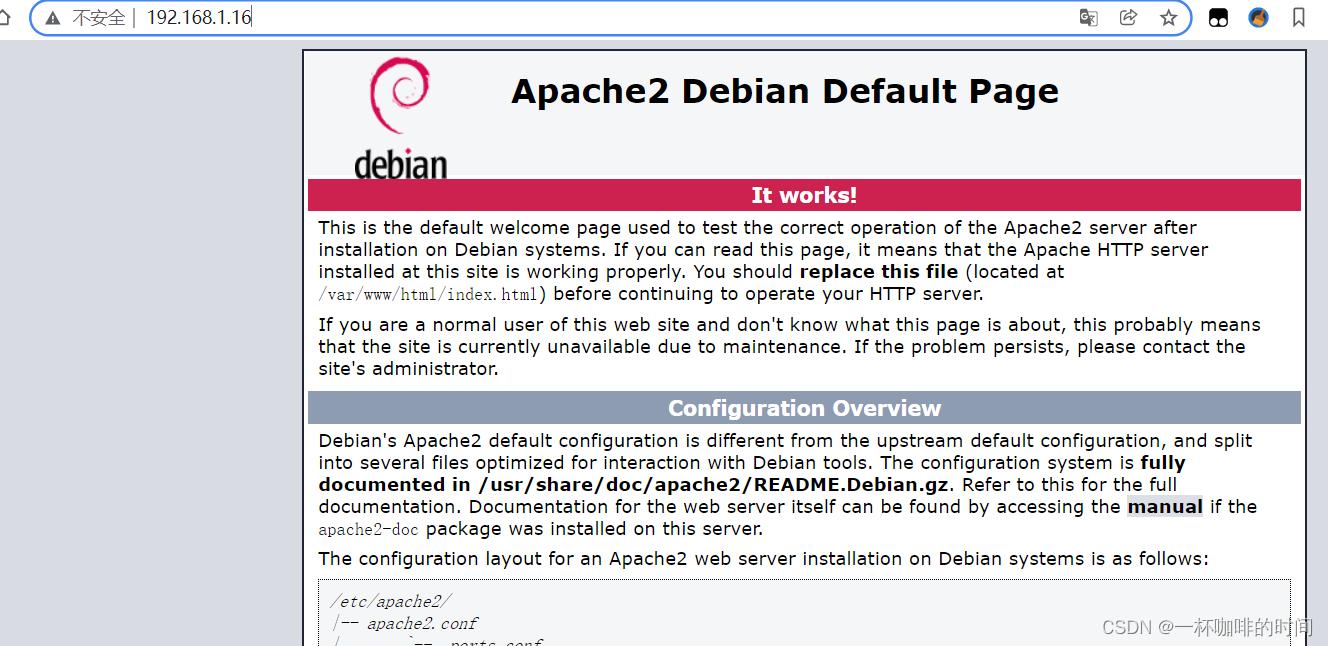
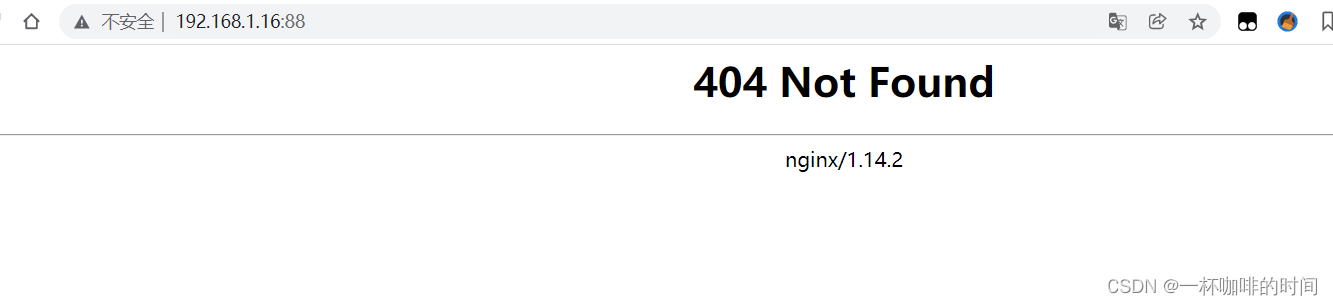
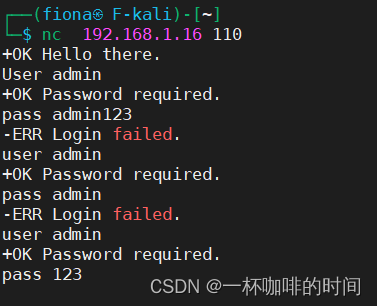
6. 通过路径遍历收集信息:
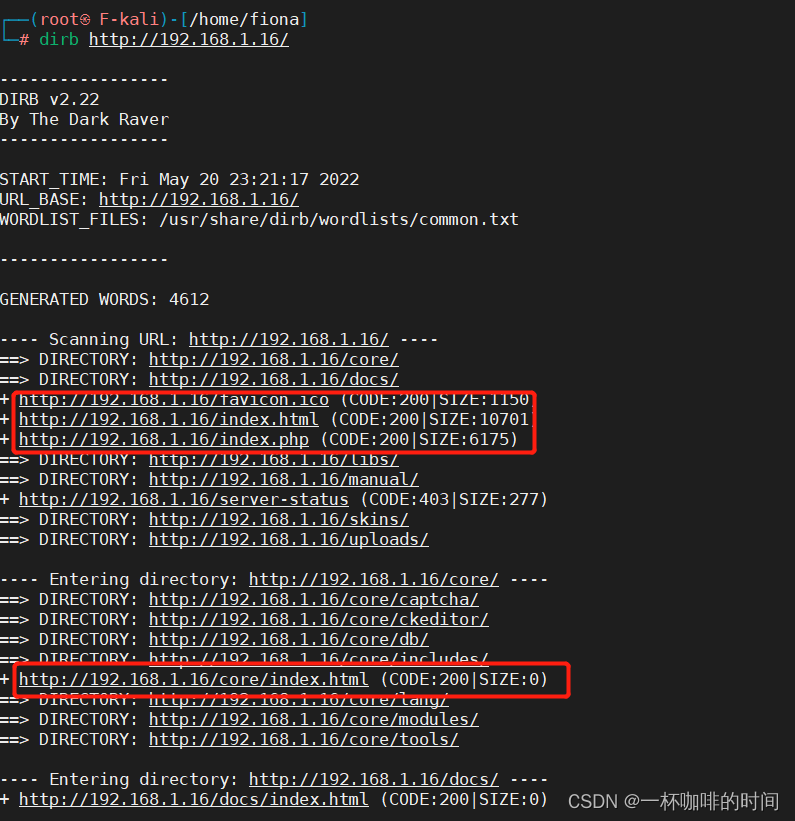
路径遍历出来的每条链接都要打开看一下。
注意:有时候单纯用一个路径遍历的工具还不行,可以同时用多个路径遍历的工具:dirsearch, nikto等很多。这边还有一点需要注意的是遍历的字典,也可以用别的字典再跑跑。
7, 根据遍历的链接打开页面如下:
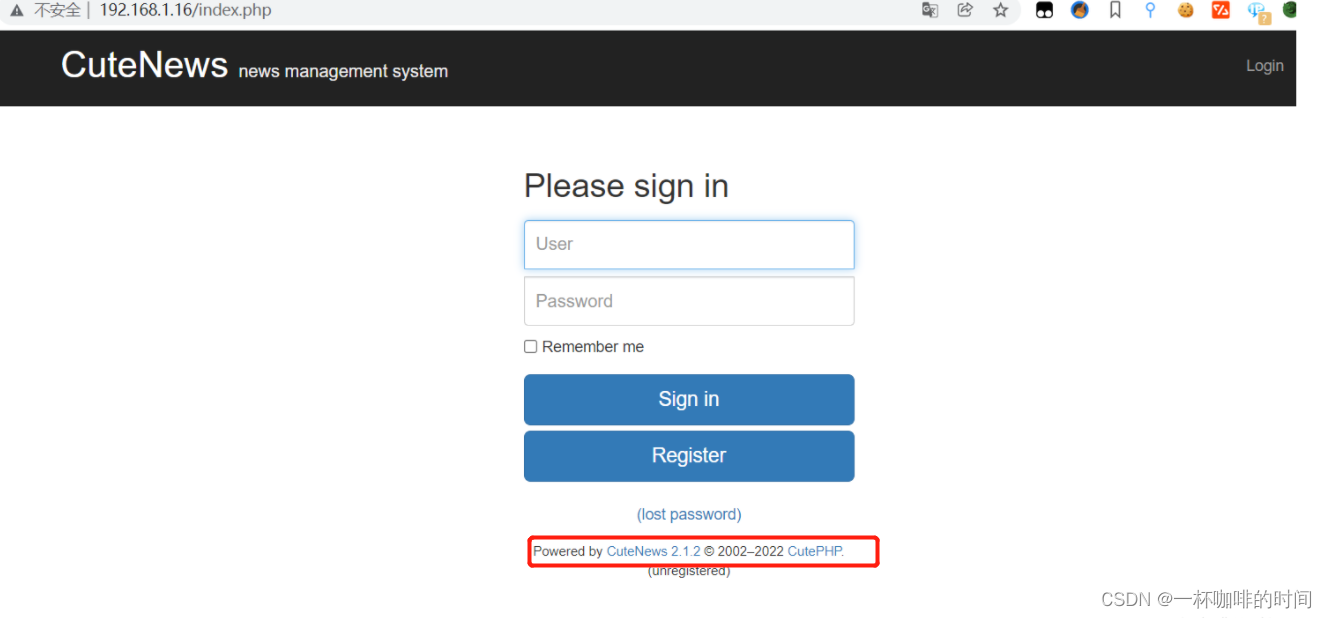
8. 根据页面上面提供的信息,搜索POC
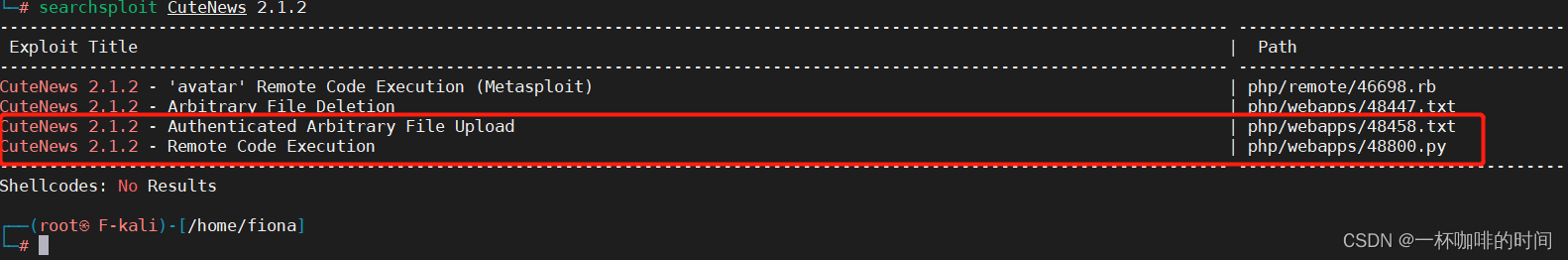
发现这边有两个POC满足要求.
后渗透阶段
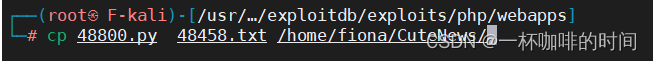
1. 终端账号获得
复制两个文件到个人目录
查找POC文件的具体目录
┌──(root㉿F-kali)-[/home/fiona]
└─# find /* -name 48458.txt
find: ‘/run/user/1000/doc’: 权限不够
find: ‘/run/user/1000/gvfs’: 权限不够
/usr/share/exploitdb/exploits/php/webapps/48458.txt┌──(root㉿F-kali)-[/home/fiona]
└─# find /* -name 48800.py
find: ‘/run/user/1000/doc’: 权限不够
find: ‘/run/user/1000/gvfs’: 权限不够
/usr/share/exploitdb/exploits/php/webapps/48800.py
更多推荐
 已为社区贡献5条内容
已为社区贡献5条内容






所有评论(0)