linux中firewalld几个使用场景
作者:【吴业亮】云计算开发工程师博客:http://blog.csdn.net/wylfengyujiancheng一、基础配置查看当前配置# firewall-cmd --get-active-zonepublicinterfaces: eth0 eth1改变域# nmcli c mod eth0 connection.zone internal# nmcli c mod
·
作者:吴业亮
博客:https://wuyeliang.blog.csdn.net/
一、基础配置
查看当前配置
# firewall-cmd --get-active-zone
public
interfaces: eth0 eth1
改变域
# nmcli c mod eth0 connection.zone internal
# nmcli c mod eth1 connection.zone external
# firewall-cmd --get-active-zone
internal
interfaces: eth0
external
interfaces: eth1
设置IP伪装
# firewall-cmd --zone=external --add-masquerade --permanent
success
# firewall-cmd --reload
success
查看配置
# firewall-cmd --zone=external --query-masquerade
yes
查看ip转发和ip伪装打开
# cat /proc/sys/net/ipv4/ip_forward
1
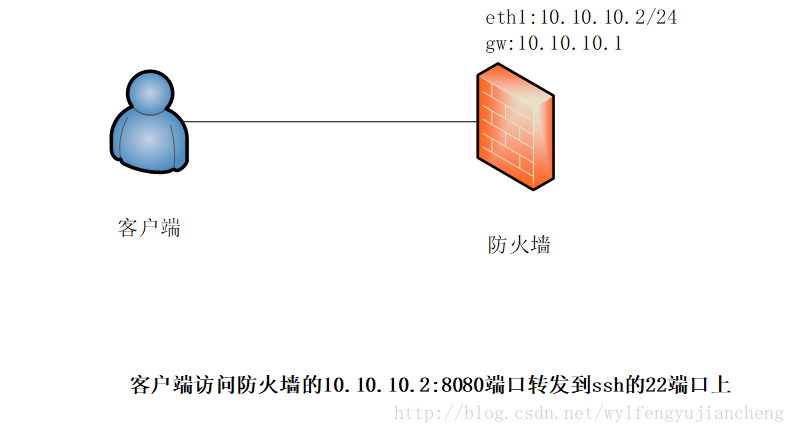
场景1、本机端口转发
访问本机external网卡的8088端口转发到本机的22号端口
# firewall-cmd --zone=external --add-forward-port=port=8088:proto=tcp:toport=22 --permanent
success
# firewall-cmd --list-all --zone=external
external (active)
interfaces: eth1
sources:
services: ssh
ports:
masquerade: yes
forward-ports: port=8088:proto=tcp:toport=22:toaddr=
icmp-blocks:
rich rules:
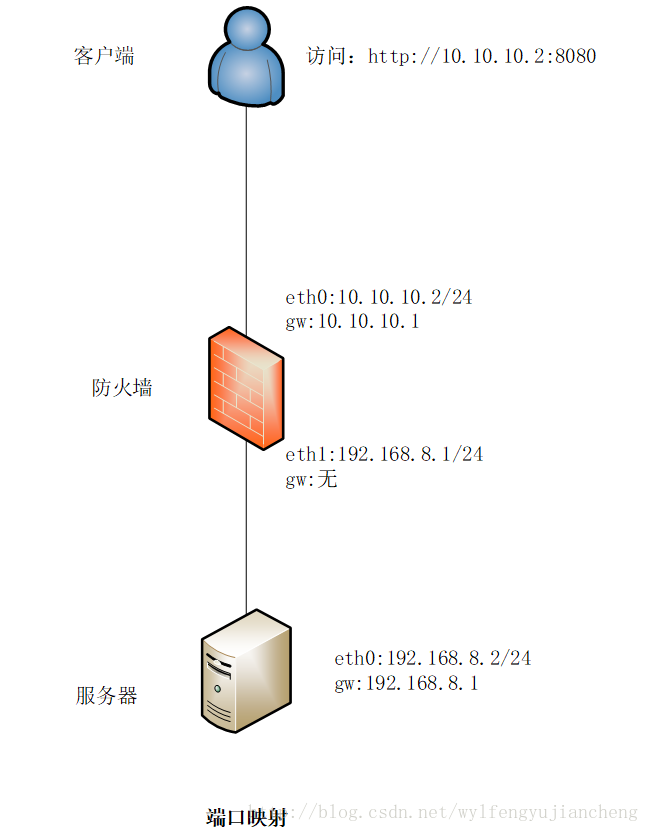
场景2:端口映射
访问防火墙的external网卡eth1的8080端口直接转发到192.168.8.2的http端口
# firewall-cmd --zone=external --add-forward-port=port=8080:proto=tcp:toport=80:toaddr=192.168.8.2 --permanent
# firewall-cmd --list-all --zone=external
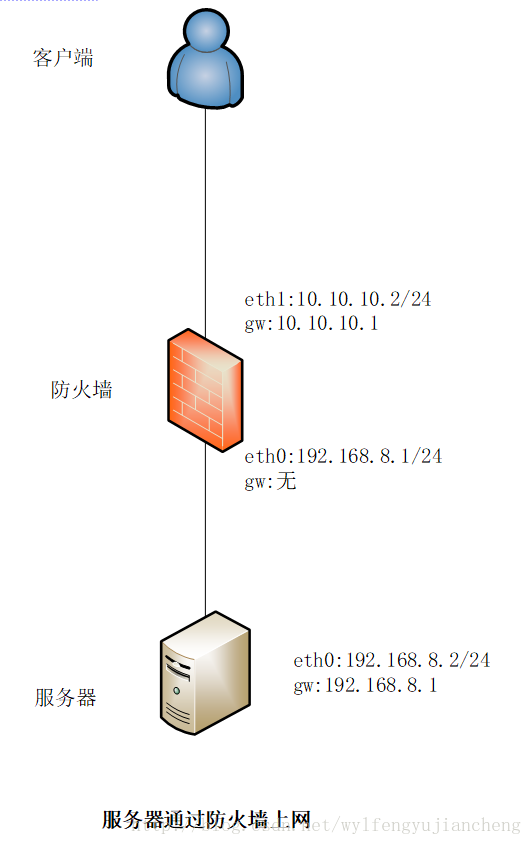
场景3:内部服务器通过防火墙上网
设置ip伪装
# firewall-cmd --zone=internal --add-masquerade --permanent
success
# firewall-cmd --reload
Success
设置网卡IP的nat
# firewall-cmd --direct --add-rule ipv4 nat POSTROUTING 0 -o eth1 -j MASQUERADE
设置规则accept
# firewall-cmd --direct --add-rule ipv4 filter FORWARD 0 -i eth0 -o eth1 -j ACCEPT
# firewall-cmd --direct --add-rule ipv4 filter FORWARD 0 -i eth1 -o eth0 -m state --state RELATED,ESTABLISHED -j ACCEPT
更多推荐
 已为社区贡献133条内容
已为社区贡献133条内容









所有评论(0)