
从零开始搭建strongswan
转眼一年就这么过去了,补下之前说到的手动搭建strongswan,免得拖到明年。准备工作一台linux服务器,这里以Debian10为例strognswan安装包,官网下载,我用的是5.9.1一.安装strongswan1) 更新,添加依赖:apt update -yapt install libpam0g-dev libssl-dev make gcc curl tcpdump -y2) 解压:
转眼一年就这么过去了,补下之前说到的手动搭建strongswan,免得拖到明年。
准备工作
一台linux服务器,这里以Debian10为例
strognswan安装包,官网下载,我用的是5.9.1
域名,这里以api.exmaple.com为例
一.安装strongswan
1) 更新,添加依赖:
apt update -y
apt install libpam0g-dev libssl-dev make gcc curl tcpdump -y2) 解压:
将strongswan安装包上传到linux服务器,解压后进入安装目录
tar -zxvf strongswan-5.9.1.tar.gz
cd strongswan-5.9.13) 配置安装:
把相关的配置参数都加上,运行
./configure --enable-eap-identity --enable-eap-md5 \
--enable-eap-mschapv2 --enable-eap-tls --enable-eap-ttls --enable-eap-peap \
--enable-eap-tnc --enable-eap-dynamic --enable-eap-radius --enable-xauth-eap \
--enable-xauth-pam --enable-dhcp --enable-openssl --enable-addrblock --enable-unity \
--enable-certexpire --enable-radattr --enable-swanctl --enable-openssl --disable-gmp最后安装
make && make install 安装完毕后会在/usr/local/etc/下生成strongswan文件
二.配置SSL证书
这里依旧用certbot申请免费证书,具体步骤可以参考这篇文章:
Certbot免费证书的安装·使用·自动续期_B★R★S的博客-CSDN博客_certbot renew
证书申请完后,生成strongswan对应的软链接:
ln -s /etc/letsencrypt/live/api.example.com/cert.pem /usr/local/etc/swanctl/x509/
ln -s /etc/letsencrypt/live/api.example.com/chain.pem /usr/local/etc/swanctl/x509ca/
ln -s /etc/letsencrypt/live/api.example.com/privkey.pem /usr/local/etc/swanctl/private/三.配置strongswan
1)新建配置文件并编辑,名称随意:
vim /usr/local/etc/swanctl/conf.d/api.example.com.conf内容如下,有中文注释的地方需要根据自身情况修改,其他不变:
connections {
ikev2-eap-mschapv2 {
version = 2
unique = never
# proposals = aes256-sha1-modp1024, aes128-sha1-modp1024, 3des-sha1-modp1024
proposals = aes256-sha256-prfsha256-modp2048, aes256gcm16-prfsha384-modp1024, default
rekey_time = 0s
pools = primary-pool-ipv4, primary-pool-ipv6
fragmentation = yes
dpd_delay = 30s
send_cert = always
local_addrs = %any
local {
certs = cert.pem
# 配置SSL证书的域名
id = api.example.com
}
remote {
auth = eap-mschapv2
eap_id = %any
}
children {
ikev2-eap-mschapv2 {
local_ts = 0.0.0.0/0,::/0
rekey_time = 0s
dpd_action = clear
# esp_proposals = aes256-sha1, aes128-sha1, 3des-sha1
esp_proposals = aes256-sha256, aes128-sha1, default
}
}
}
}
pools {
primary-pool-ipv4 {
# 防火墙虚拟ip段
addrs = 10.11.1.0/24
dns = 8.8.8.8,8.8.4.4
}
primary-pool-ipv6 {
addrs = fec1::0/16
dns = 2001:4860:4860::8888,2606:4700:4700::1111
}
}
secrets {
private-www {
file = privkey.pem
}
# id为用户名,secret为密码
eap-test {
id = test
secret = "123321"
}
}2)启用日志功能
编辑/usr/local/etc/strongswan.d/charon-logging.conf文件
filelog {
charon-debug-log {
# this setting is required with 5.7.0 and newer if the path contains dots
# path是生成日志文件的目录
path = /tmp/charon_debug.log
time_format = %a, %Y-%m-%d, %H:%M:%S
default = 2
mgr = 0
net = 1
enc = 1
asn = 1
job = 1
ike_name = yes
append = no
flush_line = yes
}
......
)四.配置防火墙
1)新建并编辑防火墙文件:
vim /etc/iptables-swan# Generated by xtables-save v1.8.2 on Tue Dec 21 09:25:40 2021
*nat
:PREROUTING ACCEPT [440:29130]
:INPUT ACCEPT [3:2180]
:POSTROUTING ACCEPT [1:68]
:OUTPUT ACCEPT [1:68]
-A POSTROUTING -s 10.11.1.0/24 -o eth0 -m policy --dir out --pol ipsec -j ACCEPT
-A POSTROUTING -s 10.11.1.0/24 -o eth0 -j MASQUERADE
COMMIT
# Completed on Tue Dec 21 09:25:40 2021
# Generated by xtables-save v1.8.2 on Tue Dec 21 09:25:40 2021
*mangle
:PREROUTING ACCEPT [14133:8077083]
:INPUT ACCEPT [5360:1107198]
:FORWARD ACCEPT [8773:6969885]
:OUTPUT ACCEPT [6322:6935214]
:POSTROUTING ACCEPT [15070:13891608]
COMMIT
# Completed on Tue Dec 21 09:25:40 2021
# Generated by xtables-save v1.8.2 on Tue Dec 21 09:25:40 2021
*raw
:PREROUTING ACCEPT [14133:8077083]
:OUTPUT ACCEPT [6322:6935214]
COMMIT
# Completed on Tue Dec 21 09:25:40 2021
# Generated by xtables-save v1.8.2 on Tue Dec 21 09:25:40 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [6322:6935214]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 80 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 443 -j ACCEPT
-A INPUT -i eth0 -p ah -j ACCEPT
-A INPUT -i eth0 -p esp -j ACCEPT
-A INPUT -i eth0 -p udp -m udp --dport 500 -j ACCEPT
-A INPUT -i eth0 -p udp -m udp --dport 4500 -j ACCEPT
-A INPUT -p udp -m udp --dport 1812 -j ACCEPT
-A INPUT -p udp -m udp --dport 1813 -j ACCEPT
-A INPUT -p tcp -m tcp --dport 8080 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -i eth0 -m policy --dir in --pol ipsec -j ACCEPT
-A FORWARD -d 10.11.1.0/24 -o eth0 -m policy --dir out --pol ipsec -j ACCEPT
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT2)使配置生效
/usr/sbin/iptables-restore < /etc/iptables-swan3)查看是否生效
/usr/sbin/iptables --listChain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT icmp -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
ACCEPT tcp -- anywhere anywhere tcp dpt:http
ACCEPT tcp -- anywhere anywhere tcp dpt:https
ACCEPT ah -- anywhere anywhere
ACCEPT esp -- anywhere anywhere
ACCEPT udp -- anywhere anywhere udp dpt:isakmp
ACCEPT udp -- anywhere anywhere udp dpt:ipsec-nat-t
ACCEPT udp -- anywhere anywhere udp dpt:radius
ACCEPT udp -- anywhere anywhere udp dpt:radius-acct
ACCEPT tcp -- anywhere anywhere tcp dpt:http-alt
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere policy match dir in pol ipsec
ACCEPT all -- anywhere 10.11.1.0/24 policy match dir out pol ipsec
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
五.配置转发和开机自启
1)开启转发
编辑/etc/sysctl.conf文件,在末尾添加以下内容
#开启内核ipv4转发
net.ipv4.ip_forward = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0
#开启内核ipv6转发
net.ipv6.conf.all.forwarding = 1使配置生效
/sbin/sysctl -p2)配置防火墙开机自启
vim /etc/network/if-pre-up.d/iptables
#!/bin/sh
/usr/sbin/iptables-restore < /etc/iptables-swan修改可执行权限
chmod +x /etc/network/if-pre-up.d/iptables3)配置strongswan开机自启
vim /etc/init.d/strongswan#!/bin/bash
/usr/local/sbin/ipsec restart && sleep 5 && /usr/local/sbin/swanctl --load-all修改可执行权限
chmod +x /etc/init.d/strongswan六.启动测试
1)启动strongswan
/etc/init.d/strongswan2)下载strongswan手机客户端
apk地址:Index of /Android
添加VPN配置如下图,此处密码对应上方配置为123321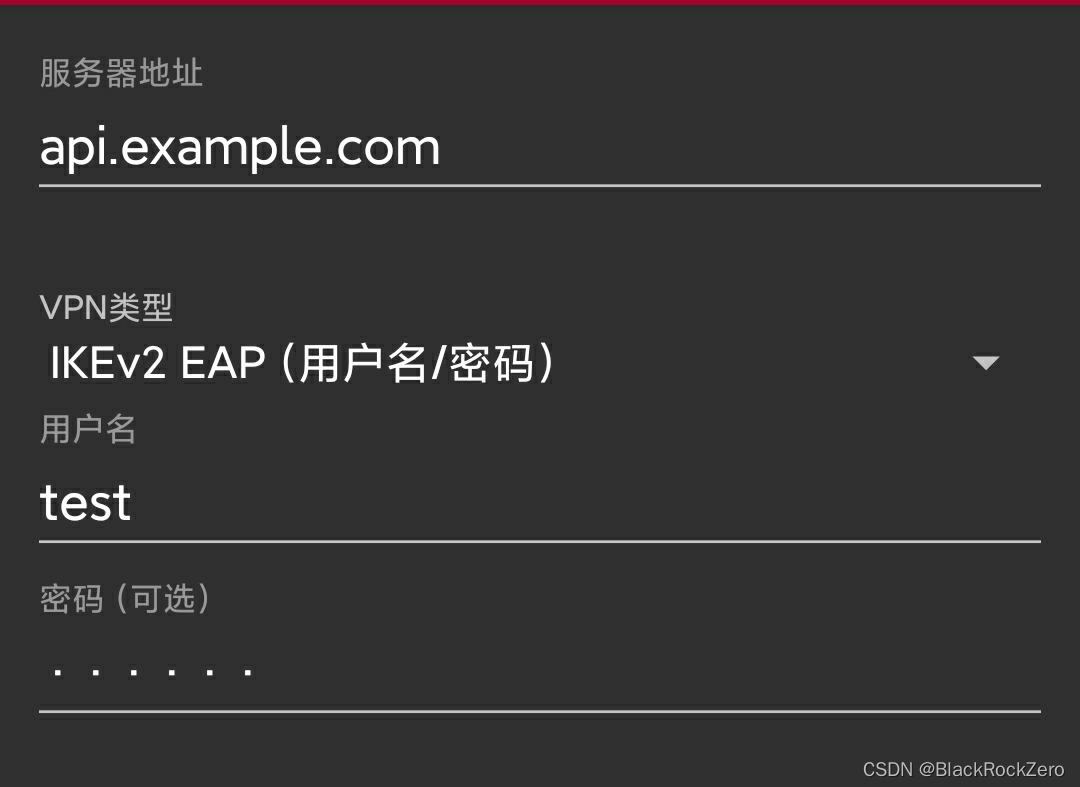
连接成功后查看ip是否变化,尝试访问其他网站,若能正常访问则大功告成
更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容









所有评论(0)